In recent years, Israeli organizations have been the primary targets of cyber espionage campaigns orchestrated by the Iranian nation-state actor known as OilRig. These campaigns, named Outer Space (2021) and Juicy Mix (2022), have revealed the group’s persistent focus on gathering sensitive information from Israeli entities. Analysis by ESET sheds light on the details of these campaigns, highlighting the tactics, techniques, and tools that OilRig employs in its cyber espionage endeavors.
OilRig: The Iranian Cyber Espionage Group
OilRig, also known by various aliases, including APT34, Cobalt Gypsy, Hazel Sandstorm, and Helix Kitten, is a cyber espionage group affiliated with Iran’s Ministry of Intelligence and Security (MOIS). This group has been active since 2014 and has consistently employed a diverse range of tools to carry out its information theft operations.
Outer Space Campaign (2021)
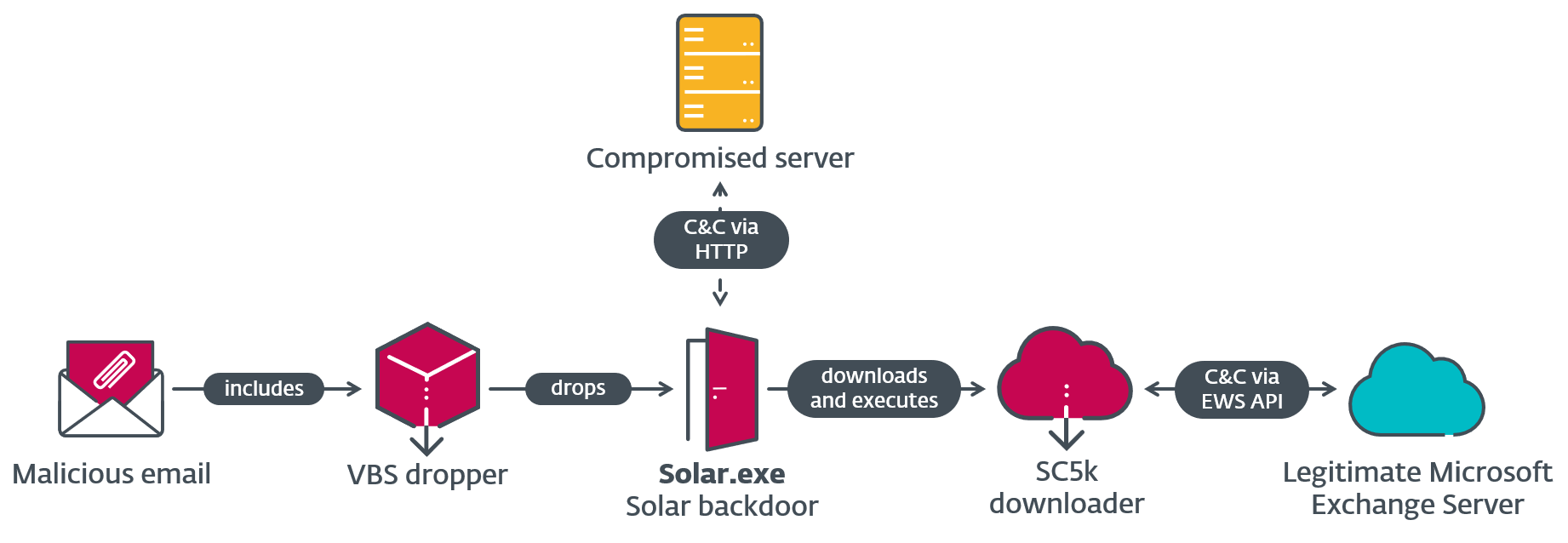
The Outer Space campaign, observed in 2021, involved OilRig compromising an Israeli human resources website. This compromised site was then repurposed as a command-and-control (C2) server for their first-stage backdoor, Solar. Solar, a C#/.NET-based backdoor, possesses basic functionality, including downloading and executing files and collecting information.
One of the notable aspects of this campaign was the deployment of a downloader named SampleCheck5000 (SC5k). SC5k utilized the Office Exchange Web Services (EWS) API to download additional tools for execution. Moreover, it included a utility called MKG, responsible for exfiltrating data from the Chrome web browser.
Juicy Mix Campaign (2022)
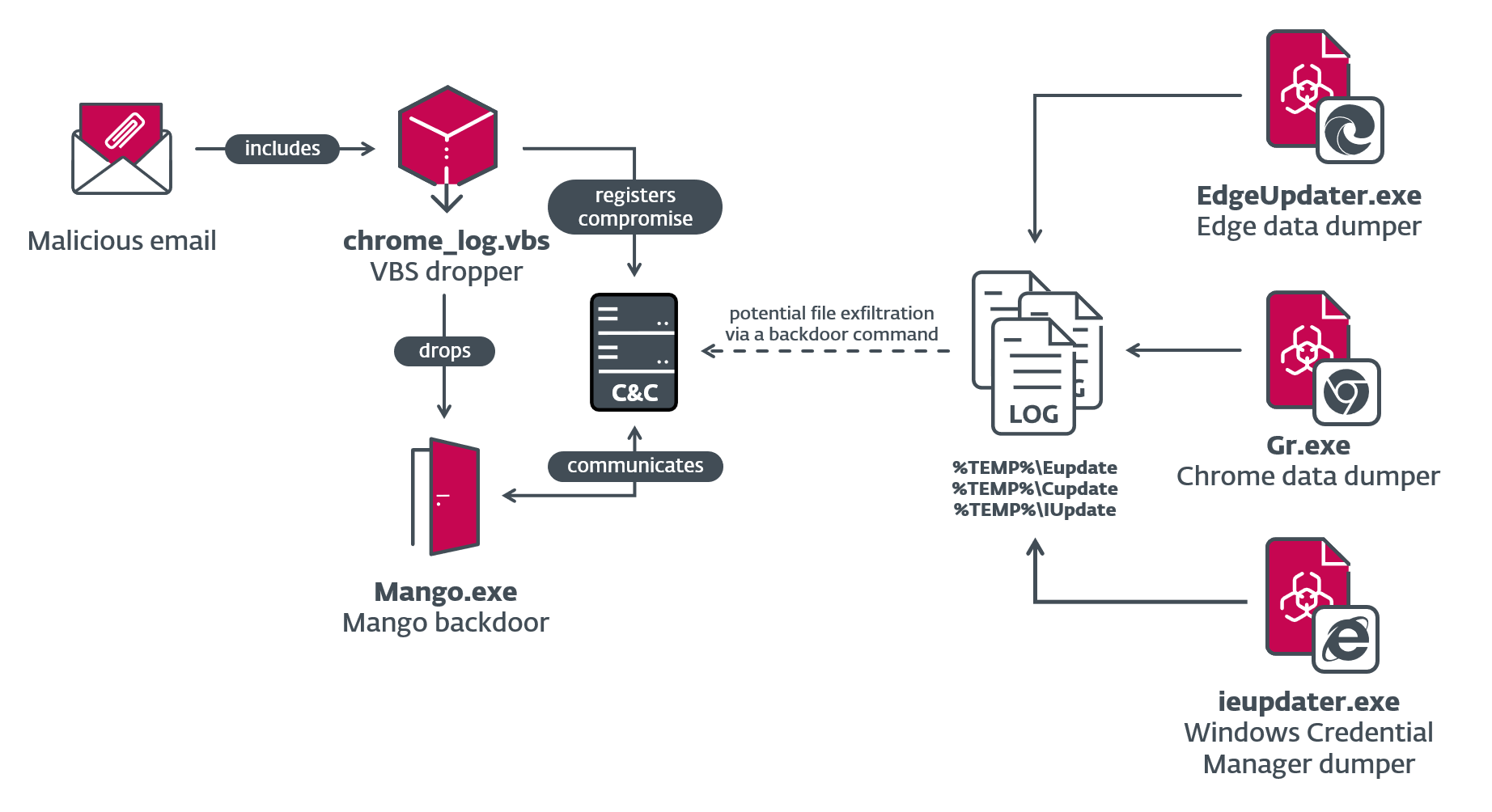
In the Juicy Mix campaign of 2022, OilRig introduced Mango, an advanced version of Solar with additional capabilities and obfuscation methods. To establish command-and-control (C2) communication, the group compromised a legitimate Israeli job portal website. The Mango malware was deployed via VBS droppers, using spear-phishing emails as the likely distribution method.
Mango featured several significant changes from Solar:
Use of Transport Layer Security (TLS) for secure C2 communications.
Using native APIs instead of .NET APIs for executing files and shell commands.
Introduction of detection evasion code.
Removal of automated data exfiltration (previously handled by the Venus task in Solar).
Additionally, two new browser-data dumping tools, CDumper and EDumper, were employed in the Juicy Mix campaign. These tools targeted the Chrome and Edge browsers, respectively, collecting cookies, browsing history, and credentials.
OilRig also employed a Windows Credential Manager stealer, known as IDumper, in the Juicy Mix campaign. This tool harvested credentials from the Windows Credential Manager and stored them in the %TEMP% directory.
Technical Analysis of Key Components
The article provides an in-depth technical analysis of the key components used in these campaigns, including the VBS droppers, Solar and Mango backdoors, SampleCheck5000 (SC5k) downloader, browser-data dumpers (CDumper and EDumper), and the Windows Credential Manager stealer (IDumper).
Conclusion
OilRig, the Iranian nation-state actor, remains a formidable force in the world of cyber espionage. Its relentless pursuit of sensitive information from Israeli organizations is evident through campaigns like Outer Space and Juicy Mix. These campaigns showcase OilRig’s ability to adapt and innovate, continuously refining its tactics and tools. As the cybersecurity landscape evolves, defenders must remain vigilant to counter the persistent threats posed by groups like OilRig.