APT41 Targets Shipping, Logistics Across Europe and Asia
APT41, a China-based cyber threat group, has been linked to an extensive campaign targeting multiple sectors worldwide. This campaign has particularly affected global shipping and logistics organizations, media and entertainment, technology, and automotive sectors across Italy, Spain, Taiwan, Thailand, Turkey, and the U.K. The group’s activities, blending state-sponsored espionage with financially motivated operations, showcase its unique modus operandi among Chinese-nexus actors.
Infiltration and Persistence
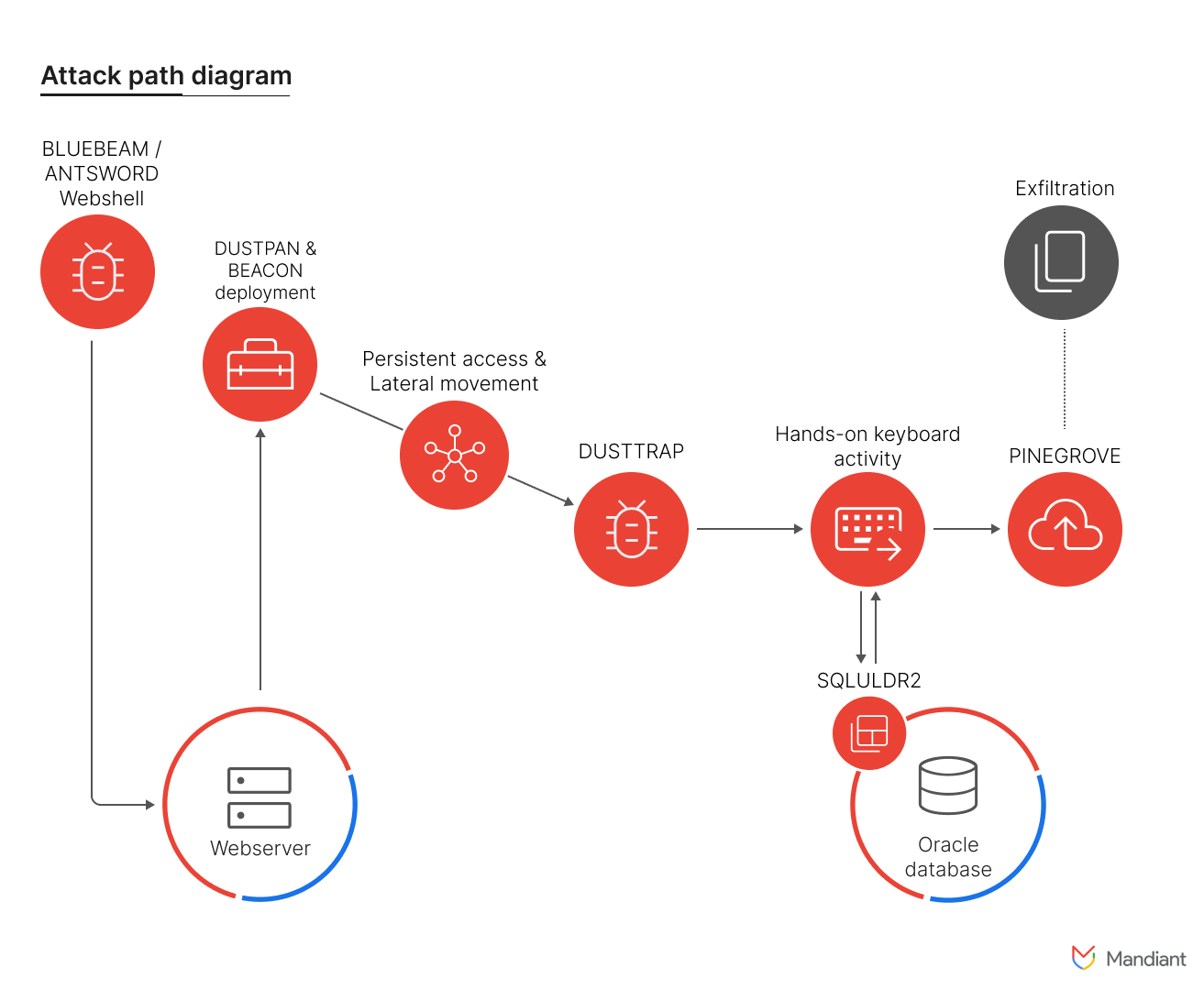
Mandiant, a Google-owned threat intelligence firm, has identified that APT41 successfully infiltrated and maintained unauthorized access to numerous networks since at least 2023. The initial access was often achieved through the deployment of ANTSWORD and BLUEBEAM web shells on Tomcat Apache Manager servers. These web shells facilitated the execution of certutil.exe to download the DUSTPAN dropper, which stealthily loaded the Cobalt Strike Beacon (BEACON) for command-and-control (C2) communication.
Escalation with DUSTTRAP
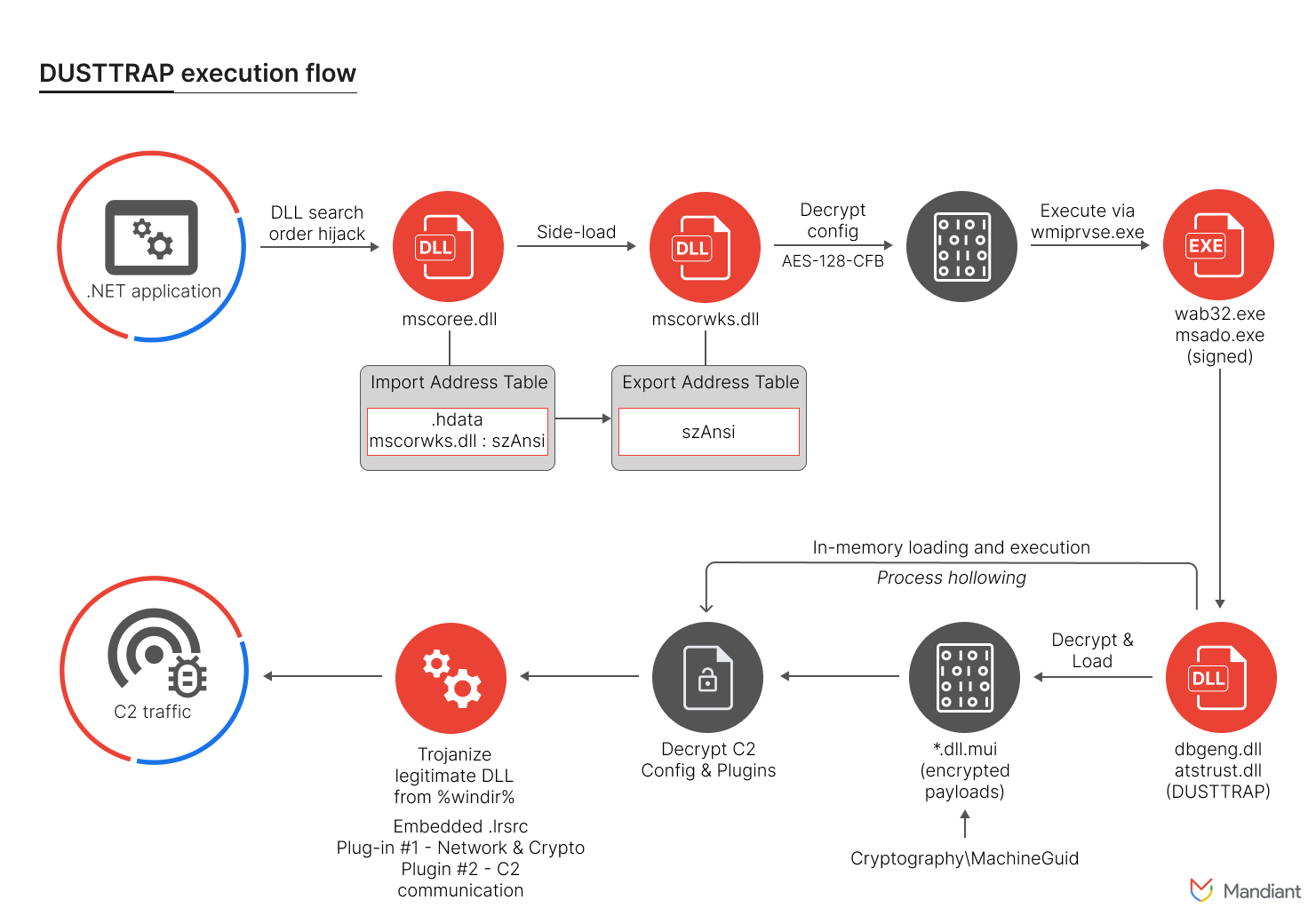
As the intrusion progressed, APT41 deployed the DUSTTRAP dropper. Upon execution, DUSTTRAP decrypted a malicious payload and executed it in memory, establishing communication channels with APT41-controlled infrastructure or compromised Google Workspace accounts. This tactic effectively concealed malicious activities within legitimate traffic. Google has since remediated the affected Workspace accounts to prevent further unauthorized access.
Advanced-Data Exfiltration Techniques
APT41’s operations are characterized by the sophisticated use of various tools to exfiltrate sensitive data. They leveraged SQLULDR2, a command-line utility, to export data from Oracle Databases to local text-based files. PINEGROVE, a command-line uploader written in Go, was used to systematically and efficiently exfiltrate large volumes of data to OneDrive, facilitating further analysis.
Impacted Sector
The impacted organizations by this attack are geographically diverse, with significant targeting of shipping and logistics sectors in Europe and the Middle East, and media and entertainment sectors in Asia. Many victimized organizations were subsidiaries or affiliates of larger multinational corporations.
Unique Malware and Techniques
APT41’s use of non-public malware typically reserved for espionage operations, such as DUSTPAN and DUSTTRAP, sets it apart from other China-nexus actors. DUSTPAN, an in-memory dropper, decrypts and executes embedded payloads, often disguised as legitimate Windows binaries. These payloads communicate using infrastructure hosted behind Cloudflare, employing advanced encryption techniques.
DUSTTRAP, a multi-stage plugin framework, further exemplifies APT41’s technical sophistication. It begins with a launcher that decrypts an on-disk PE file and executes it in memory, leading to a modular plugin system capable of a wide range of operations. These include shell operations, file system manipulations, network probing, screen capturing, and Active Directory manipulations.
Code Signing Certificates
The DUSTTRAP malware and its components were observed to be code signed with stolen certificates, often from South Korean gaming companies. This tactic aligns with APT41’s historical targeting of the video game industry for financial gain. The use of legitimate code signing certificates enhances the credibility and persistence of their malicious software.
Conclusion
APT41’s sustained and multifaceted campaign underscores the evolving threat landscape posed by state-sponsored and financially motivated cyber actors. The group’s ability to blend advanced espionage techniques with sophisticated data exfiltration strategies poses significant challenges for organizations worldwide. Ongoing vigilance, enhanced security measures, and collaboration among cybersecurity entities remain crucial in mitigating the impact of such persistent threats.


