MuddyWater Expands Tactics in Cyber Espionage Campaign to Target Israel

Recent research by cybersecurity firms Deep Instinct and Group-IB has revealed a new spear-phishing campaign conducted by the Iranian nation-state actor known as MuddyWater. This campaign, which began during the Israel-Hamas war, showcases updated Tactics, Techniques, and Procedures (TTPs) compared to MuddyWater’s previous activities.
Campaign Details:
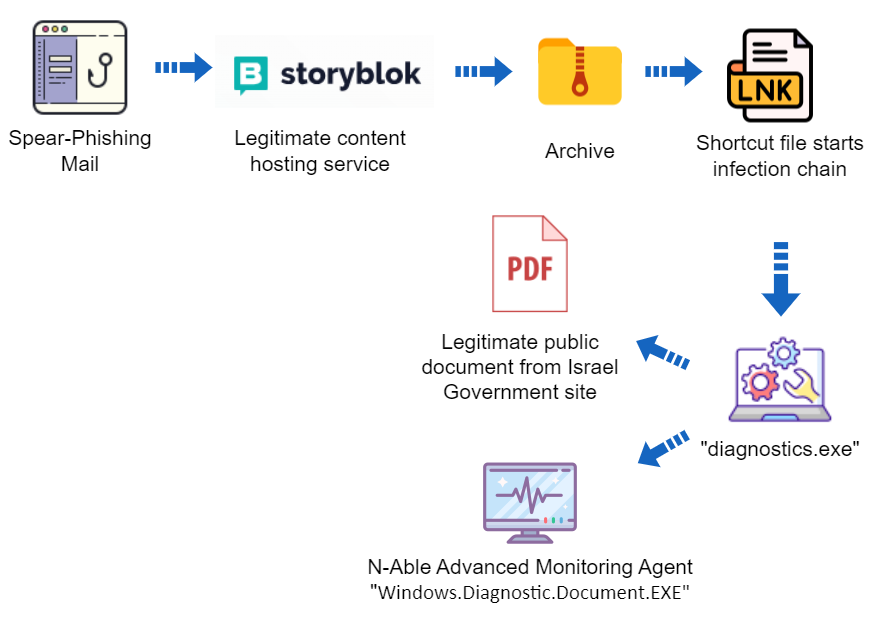
MuddyWater’s spear-phishing emails, dating back to 2020, have utilized various file formats, including direct links, PDFs, RTF, and HTML attachments. In the recent campaign, the threat actor introduced a new file-sharing service called “Storyblok.” On October 30th, Deep Instinct identified two archives on “Storyblok” containing a novel multi-stage infection vector.
Infection Vector:
The campaign likely starts with a spear-phishing email, similar to previous MuddyWater campaigns, luring victims to download an archive hosted at “a.storyblok[.]com.” In this analysis, the focus is on the “defense-video.zip” file. Upon extraction, hidden folders are revealed, including an LNK shortcut leading to an executable file called “Diagnostic.exe.”
Execution and Decoy Document:
The “Diagnostic.exe” file initiates the infection chain by executing another executable named “Windows.Diagnostic.Document.EXE,” located in a hidden directory named “.end.” This executable is a signed, legitimate installer for the “Advanced Monitoring Agent,” a remote administration tool. To deceive the victim, the LNK file also opens a Windows Explorer window of the hidden “Document” folder, making it appear as a legitimate folder. The decoy document presented to the victim is an official memo from the Israeli Civil Service Commission.
Conclusion:
MuddyWater continues its cyber espionage campaigns against Israeli targets, showcasing updated TTPs. These include using a new public hosting service, employing LNK files for initiation, and employing intermediate malware to mimic the opening of a directory while executing a new remote administration tool. After infection, the MuddyWater operator connects to the compromised host using the legitimate remote administration tool, conducts reconnaissance, and may execute PowerShell code leading the infected host to beacon a custom Command and Control (C2) server.