OPSEC Mistake Reveals North Korean Hackers in JumpCloud Breach

A significant cybersecurity breach at JumpCloud is attributed to a hacking unit affiliated with North Korea’s Reconnaissance General Bureau (RGB). The group, UNC4899, has a history of targeting cryptocurrency companies and stealing passwords from executives and security teams to fund North Korea’s nuclear weapons program. This article provides a detailed analysis of the breach, the modus operandi of the UNC4899 group, and the implications of their actions on the global cybersecurity landscape.
The Operational Security Blunder
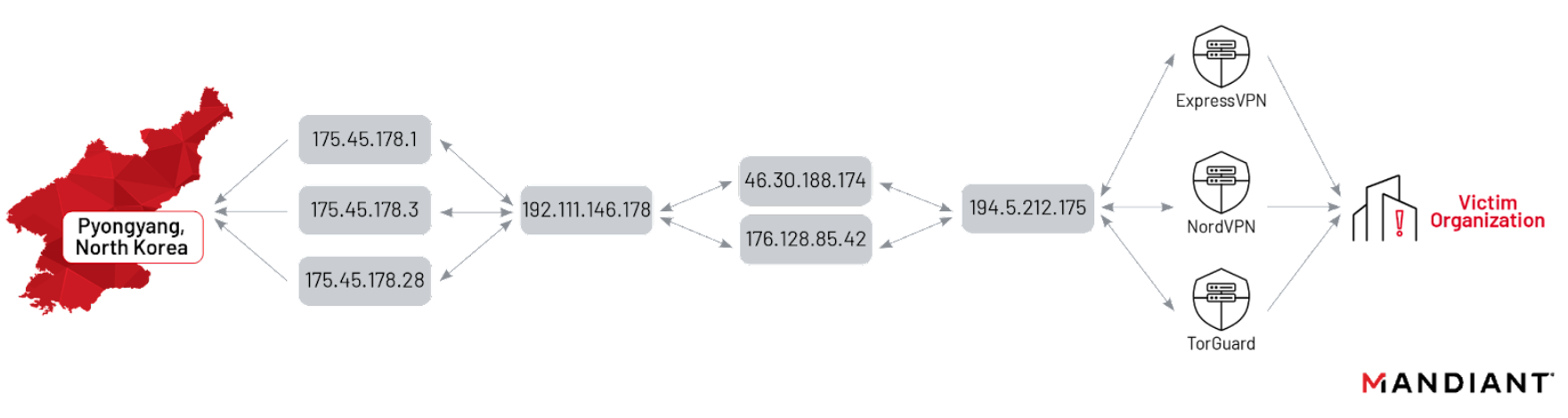
The connection between the JumpCloud breach and UNC4899 was discovered due to the North Korean hackers’ operational security (OPSEC) mistake. Typically, these state-sponsored actors use commercial VPN services to conceal their true IP addresses and locations. However, during the attack on JumpCloud, the VPNs they employed failed, exposing their real-world IP addresses, which originated from Pyongyang, North Korea. This oversight allowed cybersecurity firm Mandiant to attribute the breach to UNC4899 with high confidence. Earlier SentinelOne and CrowdStrike also attribute the attacks to the North Korean APT group.
Cryptocurrency-Focused Threat Group UNC4899
UNC4899 is a hacking group with a specific focus on cryptocurrency-related targets. Mandiant assesses that UNC4899 operates under the umbrella of North Korea’s Reconnaissance General Bureau (RGB). Their modus operandi involves using Operational Relay Boxes (ORBs) with L2TP IPsec tunnels, coupled with commercial VPN services, to mask their identities and locations. The group’s primary objective is to compromise companies dealing with cryptocurrency and fintech assets.
Previous Infrastructure Overlaps and Attribution
Mandiant’s analysis revealed that UNC4899’s attack infrastructure overlaps with previously identified hacks attributed to North Korean hackers. This discovery further solidifies the attribution of the JumpCloud breach to the RGB-affiliated group. Moreover, UNC4899 shares similarities with other North Korean hacking units, such as UNC2970 and APT43, indicating possible resource sharing and coordinated efforts within North Korea’s cyber operations.
The JumpCloud Breach
The attack on JumpCloud occurred on June 22, 2023, and involved a sophisticated spear-phishing campaign. The hackers gained unauthorized access to JumpCloud’s commands framework, allowing them to breach fewer than five customers and less than ten systems through a software supply chain attack. Interestingly, UNC4899’s focus on cryptocurrency targets extended to macOS systems, indicating a continued investment in developing tailored malware for Apple platforms.
Malicious Payloads and Techniques
UNC4899 employed several malicious payloads and techniques during the JumpCloud breach:
FULLHOUSE.DOORED: A C/C++-based first-stage backdoor that communicates via HTTP, capable of shell command execution, file transfer, file management, and process injection.
STRATOFEAR: A second-stage modular implant designed to gather system information and retrieve or execute additional modules from remote servers or local disk storage.
TIEDYE: A second-stage Mach-O executable capable of communicating with a remote server, running additional payloads, gathering basic system information, and executing shell commands. TIEDYE exhibits similarities to the backdoor RABBITHUNT, used in previous North Korean campaigns.
Financially Motivated Operations
The JumpCloud breach aligns with other financially motivated attacks by North Korean actors targeting cryptocurrency and fintech-related assets. This indicates an increased emphasis on using supply chain tactics to compromise select entities and achieve their objectives. Moreover, using open-source packages for malware distribution presents a significant challenge for cybersecurity professionals worldwide.