Surge in USB-Based Cyber Espionage Campaigns Raises Security Concerns

In the first half of 2023, cybersecurity experts have witnessed a significant increase in cyber attacks utilizing infected USB drives as an initial access vector. This alarming trend, identified by Mandiant, highlights the growing threat posed by USB-based campaigns targeting both public and private sector organizations worldwide. There are two prominent malware campaigns, SOGU and SNOWYDRIVE, targeting public and private sector entities worldwide.
The SOGU Campaign:
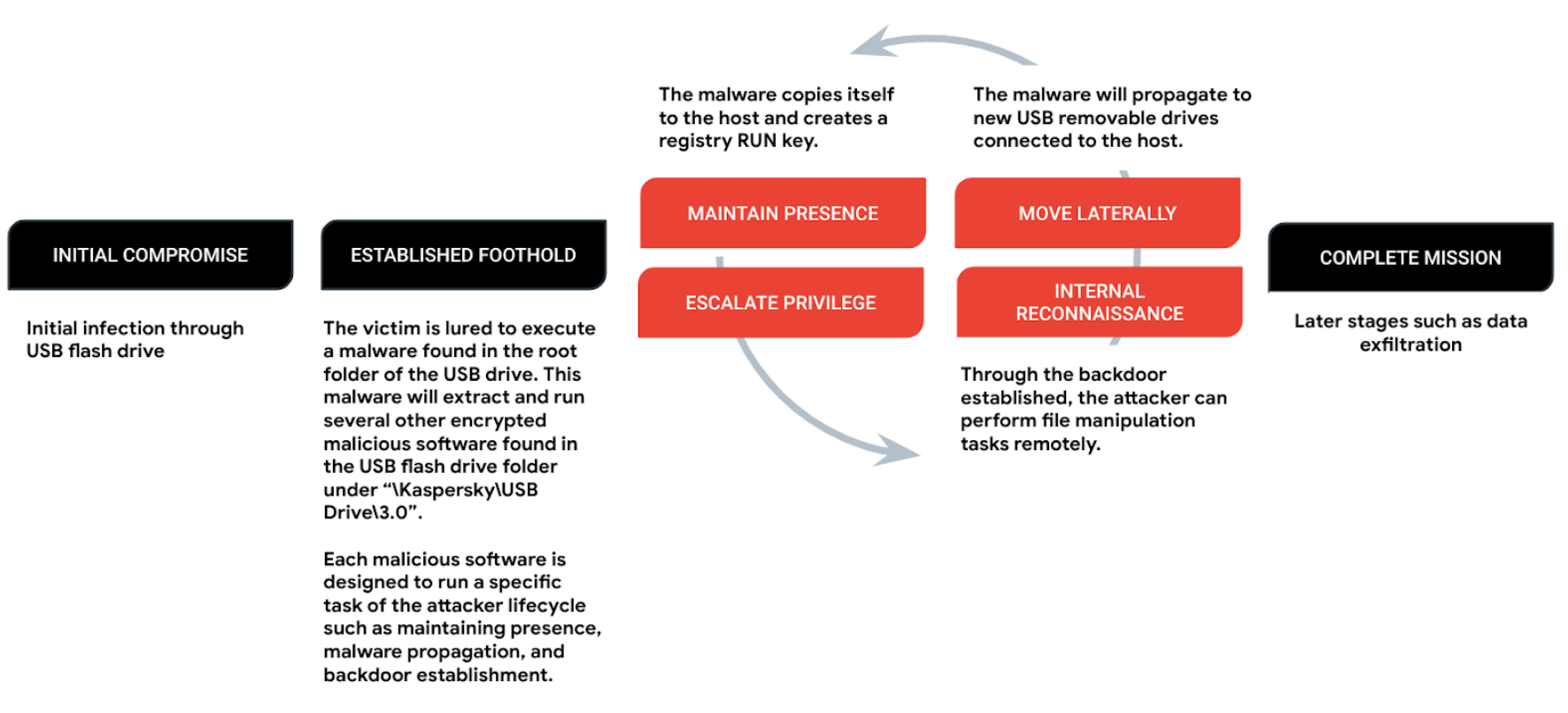
One of the most aggressive USB-based cyber espionage attacks is the SOGU campaign, attributed to TEMP.Hex, a China-linked cyber espionage actor. SOGU targets various industries, including construction, engineering, business services, government, health, transportation, and retail across Europe, Asia, and the United States. The infection chain begins with a malicious USB flash drive, leading to the execution of PlugX (also known as Korplug). This initiates the launch of the SOGU backdoor, which enables the theft of sensitive information through file exfiltration, keystroke logging, and screenshot capture.
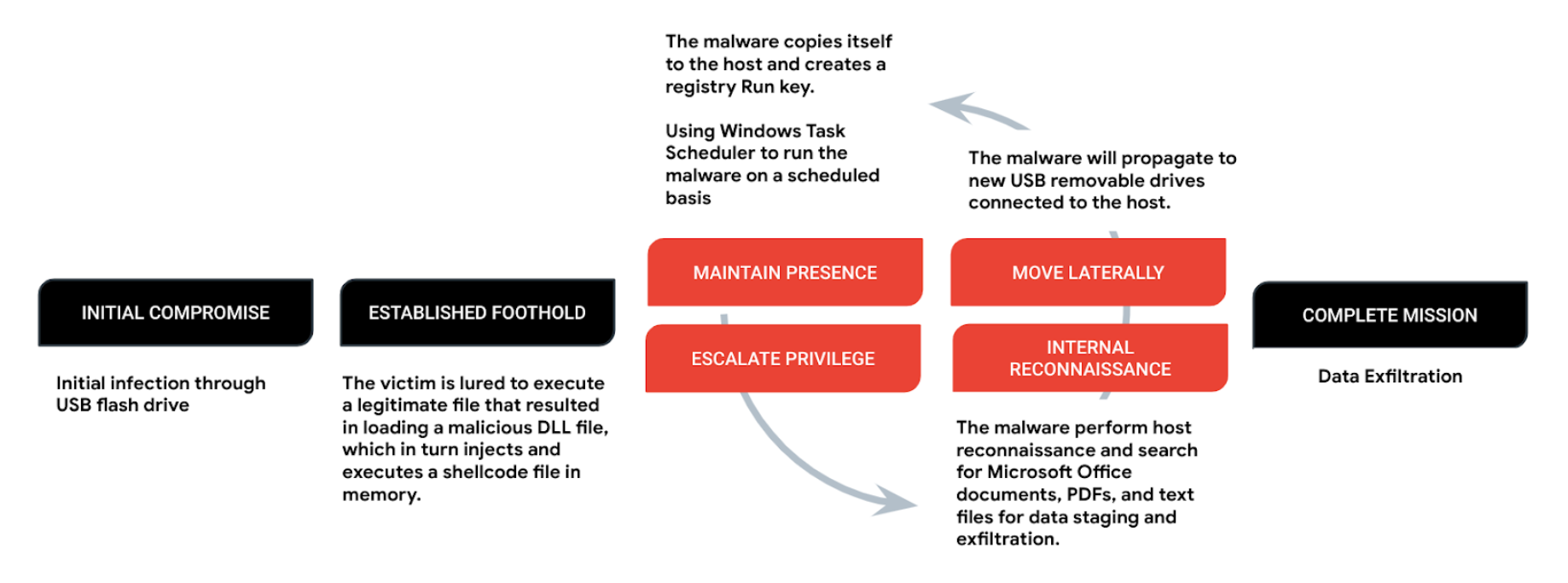
The SNOWYDRIVE Campaign:
Another significant USB-based campaign, SNOWYDRIVE, specifically targets oil and gas organizations in Asia. Attributed to UNC4698, this campaign employs USB flash drives as a delivery mechanism for the SNOWYDRIVE malware. Once infected, the malware establishes a backdoor on the compromised system, granting remote access and the ability to execute arbitrary payloads. SNOWYDRIVE spreads to other USB flash drives, facilitating lateral movement within the network and posing a serious threat to the targeted organizations.
Commonalities and Implications:
Both SOGU and SNOWYDRIVE campaigns exploit the use of infected USB drives, taking advantage of their ability to bypass security mechanisms and gain initial access to corporate networks. These attacks underscore the risks associated with USB drives, as they can potentially infect air-gapped systems that are isolated for security reasons.
To combat these threats, organizations are urged to implement restrictions on external device access, such as USB drives. If restrictions are not feasible, conducting thorough scans for malicious files or code before connecting USB drives to internal networks is essential. Additionally, maintaining awareness of infection hotspots, such as print shops and hotels, can aid in preventing the spread of USB-based malware.
Conclusion:
The surge in USB-based cyber espionage campaigns highlights the evolving tactics employed by threat actors to infiltrate organizations’ systems and steal sensitive data. The SOGU and SNOWYDRIVE campaigns are prominent examples of these attacks’ growing sophistication and reach. By prioritizing security measures such as access restrictions and comprehensive scanning, organizations can mitigate the risks associated with infected USB drives and safeguard their networks from these persistent threats.