Cybersecurity researchers at Check Point Research have uncovered a series of coordinated cyber-espionage campaigns targeting government and law enforcement organizations across Southeast Asia. The activity, first discovered and documented by the firm, has been grouped under the codename “Amaranth-Dragon.”
The campaigns ran from March through October 2025 and affected targets in Cambodia, Thailand, Laos, Indonesia, Singapore, and the Philippines. Across all operations, the attackers showed careful alignment with local political events, government programs, and official ceremonies. Filenames referenced real meetings, salary decisions, training exercises, and even a coast guard anniversary, making the malicious files appear credible at first glance.
A key shift occurred in mid-August when the group began exploiting a newly disclosed WinRAR vulnerability, tracked as CVE-2025-8088. The flaw was disclosed on August 8. Public exploit code appeared on GitHub on August 14. By August 18, Amaranth-Dragon was already using it in live campaigns.
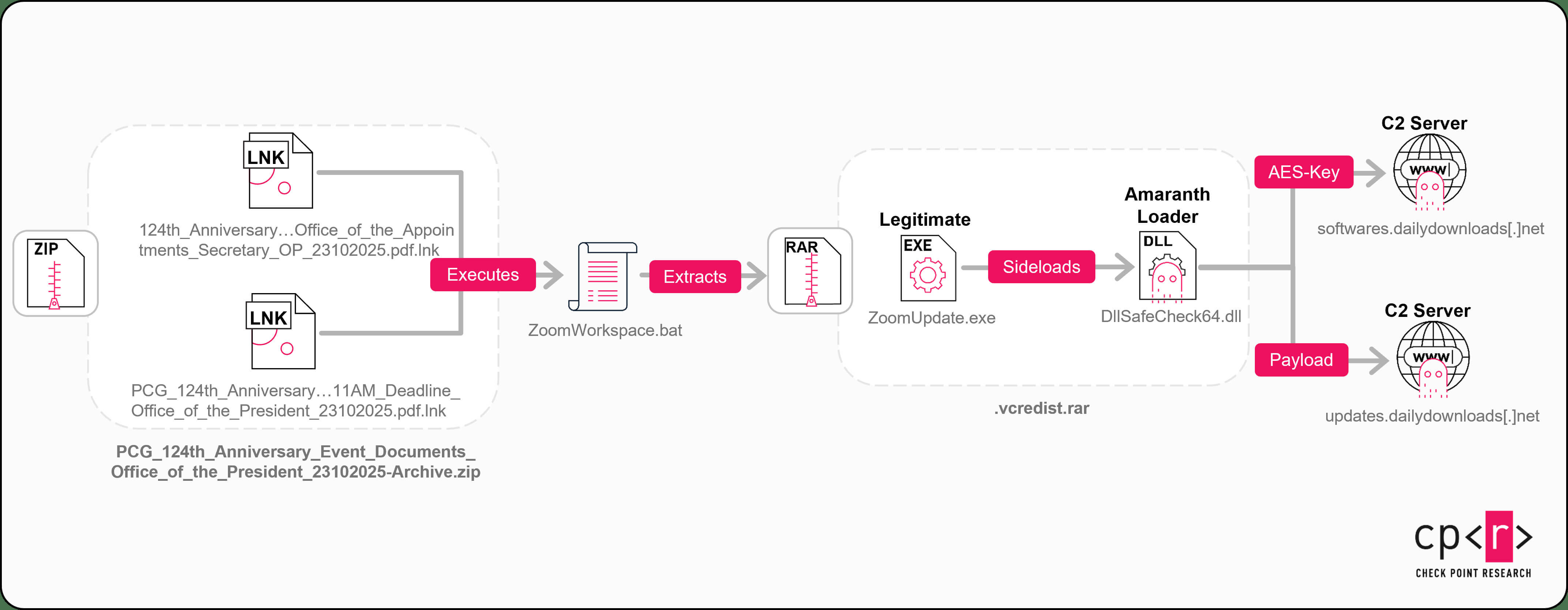
The vulnerability allowed attackers to craft malicious RAR archives that silently dropped scripts into the Windows Startup folder. When the victim rebooted the machine, the system executed the attacker’s code automatically. The speed with which the group adopted the exploit illustrates how quickly advanced actors now operationalize newly published vulnerabilities.
Once triggered, victims did not see traditional malware. A legitimate signed program sideloaded a malicious DLL known as the Amaranth Loader. That loader contacted remote infrastructure to retrieve an AES encryption key, initially from Pastebin and later from attacker-controlled servers. Using this key, it decrypted a payload and executed it directly in memory, leaving very little forensic evidence on disk.
In most cases, that payload was the Havoc Framework, an open-source command-and-control platform designed for penetration testing and red teaming. Repurposed for malicious use, Havoc gave the attackers a mature post-exploitation toolkit for remote control, data collection, and movement inside compromised networks.
The command infrastructure behind these attacks was unusually disciplined. Servers were hidden behind Cloudflare and configured to respond only to IP addresses from the intended target country. Requests from outside that geography received an HTTP 403 error. This restriction did more than limit unintended infections. It allowed researchers to reliably determine which country each campaign was designed to hit, based on which IP ranges were permitted to retrieve the payload.
One September campaign stood out. Instead of deploying the loader and Havoc, the attackers delivered a custom remote access tool called TGAmaranth RAT. This malware used a hardcoded Telegram bot as its command channel. Operators could issue commands, capture screenshots, download files, and execute shell instructions through the Telegram API. The shift from Pastebin-delivered keys and Havoc shellcode to a Telegram-based RAT suggests either parallel tooling within the group or an operational pivot for specific targets.
Several technical traits link Amaranth-Dragon to tooling previously associated with the Chinese threat group APT41. These include DLL sideloading techniques, distinctive coding patterns where unused exports point to sleep loops, and development artifacts tied to Crypto++ libraries. Compilation timestamps and campaign timing consistently aligned with the UTC+8 time zone, matching China Standard Time. Check Point Research stops short of definitive attribution but notes these overlaps as significant.
The final observed campaign coincided with the 124th anniversary of the Philippine Coast Guard. Files impersonating the Office of the President were used as bait. Even extracting and running a single shortcut file triggered the unpacking of the entire archive and execution of hidden scripts.
Why this matters
These campaigns show how advanced tradecraft is becoming easier to assemble. Within days of public exploit code appearing online, the group integrated it into targeted espionage operations. They combined a newly disclosed vulnerability, legitimate cloud hosting services, signed executables, open-source offensive frameworks, and tightly geo-restricted infrastructure into a coherent attack chain. Capabilities once associated only with elite threat actors are becoming more modular and portable.
For defenders, indicators included repeated use of Pastebin accounts such as amaranthbernadine, infrastructure patterns under domains like dailydownloads.net, and a distinctive AES initialization vector used across loader samples. Check Point Research has published a full list of indicators of compromise and YARA rules alongside the report to help organizations detect related activity.
The findings underline the importance of rapid patching, scrutiny of archive files from external sources, and monitoring for unusual outbound connections to seemingly benign domains. For government and critical infrastructure organizations in the region, these campaigns demonstrate how closely cyber operations can mirror real-world political timelines.
The initial discovery and analysis of Amaranth-Dragon by Check Point Research provides rare visibility into how a modern, disciplined espionage campaign unfolds across multiple countries over time.