In the vast landscape of cybersecurity threats, the discovery of StripedFly malware has sent shockwaves through the industry. Initially dismissed as just another cryptocurrency miner, this malware has proven to be a sophisticated and multi-faceted threat, employing an intricate modular framework that operates seamlessly on both Linux and Windows platforms. Behind its cryptocurrency mining facade lies a complex network of features, including a built-in TOR network tunnel, communication via trusted services like GitLab and GitHub, and a unique propagation pattern that sets it apart from conventional malware.
The Genesis:
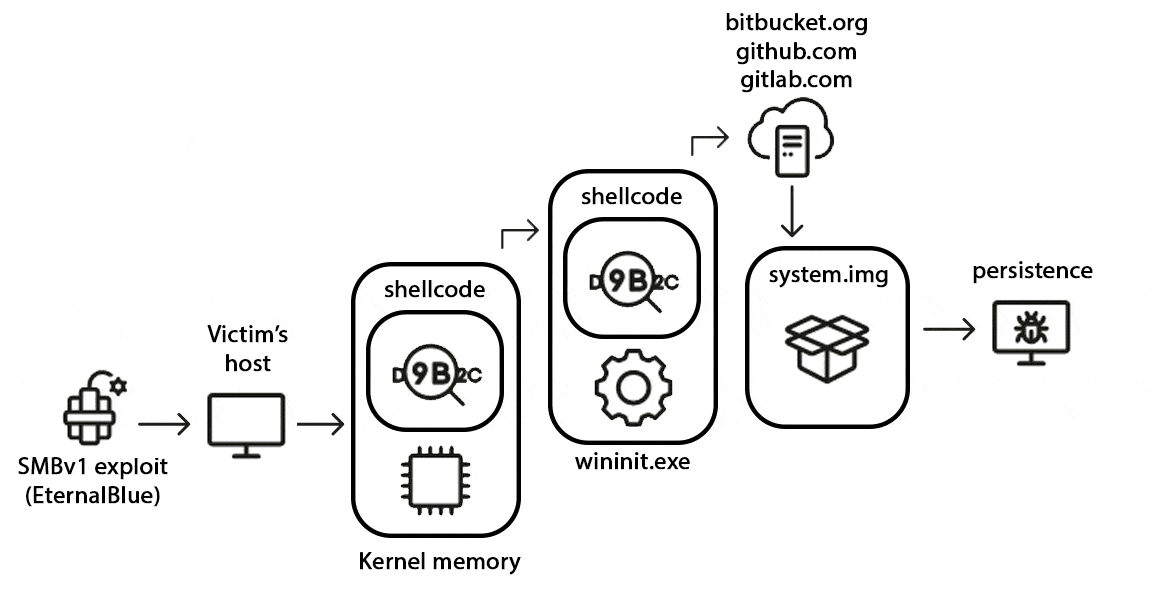
The journey of unraveling StripedFly began in 2022 when two unexpected detections surfaced within the WININIT.EXE process, echoing earlier traces of the Equation malware. Subsequent analysis exposed a code dating back to 2017, previously misclassified as a cryptocurrency miner. However, deeper investigation revealed that mining was merely a decoy for its primary objective.
Infiltration and Propagation:
StripedFly employs a custom EternalBlue SMBv1 exploit for infiltration, executed before the exploit’s public disclosure in April 2017 by the Shadow Brokers group. The malware’s distinctive propagation pattern allows it to quietly spread within local networks, utilizing both the SMB protocol and SSH keys found on victim machines.
Persistence Mechanisms:
The malware exhibits diverse persistence mechanisms depending on the availability of PowerShell and the privileges of the process. Whether running with administrative or user-level privileges, StripedFly ensures its continued presence through hidden files, registry entries, and scheduled tasks.
Bitbucket Repository:
To minimize its initial footprint, StripedFly encapsulates elements in an encrypted and compressed custom binary archive hosted on legitimate websites, disguised as firmware binaries for mysterious devices labeled “m100.” The Bitbucket repository, created under the account of Julie Heilman, serves as a discreet hub for malware updates.
TOR Network Communication:
StripedFly communicates with its command and control (C2) server residing in the TOR network, utilizing a custom lightweight TOR client. This unique implementation, devoid of known open-source TOR features, showcases the malware’s dedication to hiding its C2 server at all costs.
Modular Architecture:
The malware’s payload is structured as a monolithic binary executable code, supporting pluggable modules for extending or updating functionality. Divided into service and extended functionality modules, these components handle configuration storage, upgrade/uninstall processes, reverse proxy functionalities, miscellaneous command handling, credential harvesting, repeatable tasks, reconnaissance, and infection modules.
Monero Cryptocurrency Mining:
One notable module disguises itself as a chrome.exe process, engaging in Monero cryptocurrency mining. The module ensures effective masquerading, reporting mining statistics to the C2 server and concealing DNS resolutions behind DNS over HTTPS requests to Cloudflare.
Connection to ThunderCrypt Ransomware:
During the analysis, a connection to the ThunderCrypt ransomware variant was uncovered, sharing the same codebase and communicating with the same C2 server. This revelation adds another layer of complexity to StripedFly’s history and purpose.
Parallels with EternalBlue:
A timeline analysis suggests parallels between StripedFly’s incorporation of the EternalBlue exploit and the activities of the Shadow Brokers group. The malware’s appearance coincides with significant events in the cybersecurity landscape, including the WannaCry ransomware attack and the release of the EternalBlue exploit.
Conclusion:
StripedFly stands as a testament to the evolving sophistication of cyber threats. Its true purpose remains shrouded in mystery, with the malware creators leaving experts puzzled. While the presence of ThunderCrypt ransomware implies a potential commercial motive, the decision to focus on cryptocurrency mining raises questions about the malware’s ultimate goal. The enigma surrounding StripedFly highlights the need for continued vigilance and research in the ever-evolving landscape of cybersecurity.