Starkcat and HotPage Malware Target Critical Infrastructure and Browser Traffic
The cybersecurity landscape is ever-evolving, with new threats emerging regularly. Two recent discoveries, the Starkcat and HotPage malware, have drawn significant attention due to their sophisticated methodologies and potential impacts.
Origin and Discovery
Starkcat, identified by cybersecurity researchers at ESET as a significant new threat, originated from an unknown but highly capable group. This malware has been designed with a high degree of sophistication, suggesting the involvement of advanced persistent threat (APT) actors. Its initial detection was linked to targeted attacks on financial institutions and critical infrastructure, signaling its potential for significant disruption.
Methodology and Techniques
Starkcat employs a multi-stage infection process, beginning with a phishing campaign that delivers a malicious payload. Once the initial payload is executed, it leverages a series of exploits to escalate privileges and establish persistence on the victim’s system. Notably, Starkcat utilizes polymorphic techniques to evade detection by traditional antivirus software. Its command-and-control (C2) infrastructure is robust, employing encrypted communications to prevent interception and analysis.
Impact and Implications
The impact of Starkcat is profound, with the ability to exfiltrate sensitive data, disrupt operations, and potentially cause physical damage to critical infrastructure. There is a need for heightened vigilance and advanced security measures to detect and mitigate such sophisticated threats. The financial sector, in particular, has been urged to adopt proactive defenses, given its attractiveness as a target for Starkcat.
Discovery and Background
HotPage malware represents another alarming cybersecurity threat. Discovered through a joint effort by cybersecurity researchers and law enforcement agencies, HotPage is known for its deceptive capabilities and extensive reach. The malware was initially identified through anomalous browser traffic, leading to a deeper investigation that uncovered its complex mechanisms.
Technical Analysis
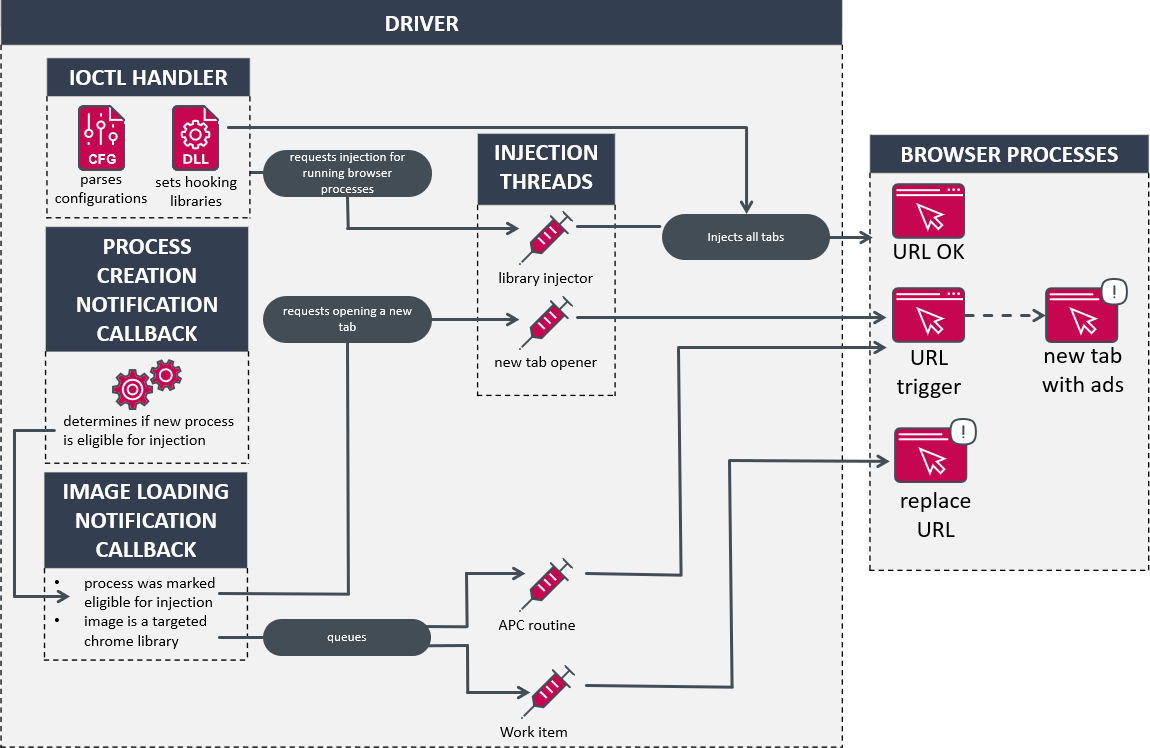
HotPage operates by exploiting a signed driver, a technique that allows it to bypass many security controls. This driver facilitates browser traffic tampering, redirecting users to malicious sites, or injecting malicious code into legitimate websites. HotPage’s use of a signed driver is particularly concerning, as it undermines the trust model inherent in digital certificates.
The malware’s C2 infrastructure is highly decentralized, utilizing a peer-to-peer network to communicate with infected devices. This makes it challenging to dismantle, as there is no single point of failure. Additionally, HotPage employs advanced obfuscation techniques to remain hidden on infected systems, complicating detection and remediation efforts.
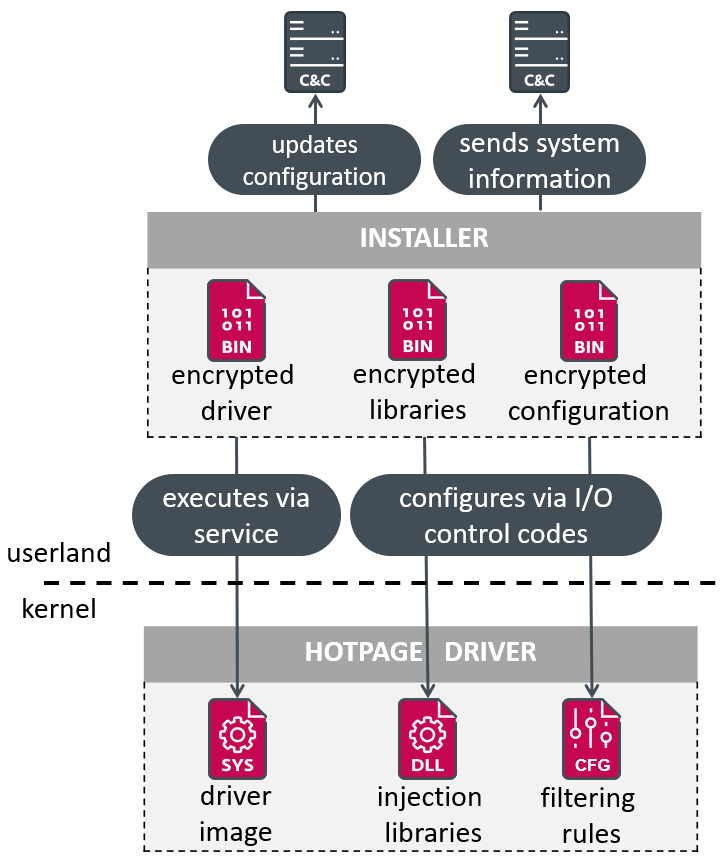
Consequences and Countermeasures
HotPage’s ability to manipulate browser traffic poses significant risks to both individuals and organizations. It can facilitate credential theft, financial fraud, and the spread of additional malware. Robust endpoint protection and network monitoring are essential to detect and mitigate such threats. Furthermore, the discovery of HotPage has prompted renewed calls for stricter controls on the issuance and management of digital certificates.
Comparative Analysis
While Starkcat and HotPage differ in their primary targets and methodologies, they share common themes of sophistication and potential for significant impact. Both malware variants demonstrate the evolving nature of cyber threats and the need for continuous advancements in cybersecurity defenses.
Similarities
Sophistication: Both Starkcat and HotPage employ advanced techniques to evade detection and maintain persistence.
C2 Infrastructure: Both utilize robust, encrypted communications for their C2 operations, complicating efforts to intercept and analyze their traffic.
Impact: Both have the potential to cause severe damage, whether through data exfiltration (Starkcat) or browser traffic manipulation (HotPage).
Differences
Targets: Starkcat primarily targets financial institutions and critical infrastructure, while HotPage is more focused on manipulating browser traffic across various targets.
Techniques: Starkcat relies heavily on phishing and exploits for initial infection, whereas HotPage leverages a signed driver for its operations.
Conclusion
The discoveries of Starkcat and HotPage malware underscore the dynamic and ever-evolving nature of cybersecurity threats. As these threats grow more sophisticated, so must the defenses against them. Organizations must adopt a proactive stance, leveraging advanced security technologies and practices to protect against these and other emerging threats. Continuous vigilance, collaboration among cybersecurity professionals, and the implementation of robust security measures are crucial to mitigating the risks posed by sophisticated malware like Starkcat and HotPage.


