New Android Malware CherryBlos Target Users using OCR
A new wave of Android malware campaigns has been discovered, posing significant risks to cryptocurrency users and unsuspecting victims. The malware strains, named CherryBlos and FakeTrade, employ advanced techniques to steal sensitive information and conduct fraudulent activities. Security researchers from Trend Micro have identified the threat actors behind these campaigns and the various distribution channels used to infect devices.
CherryBlos: An Advanced Cryptocurrency Stealer:
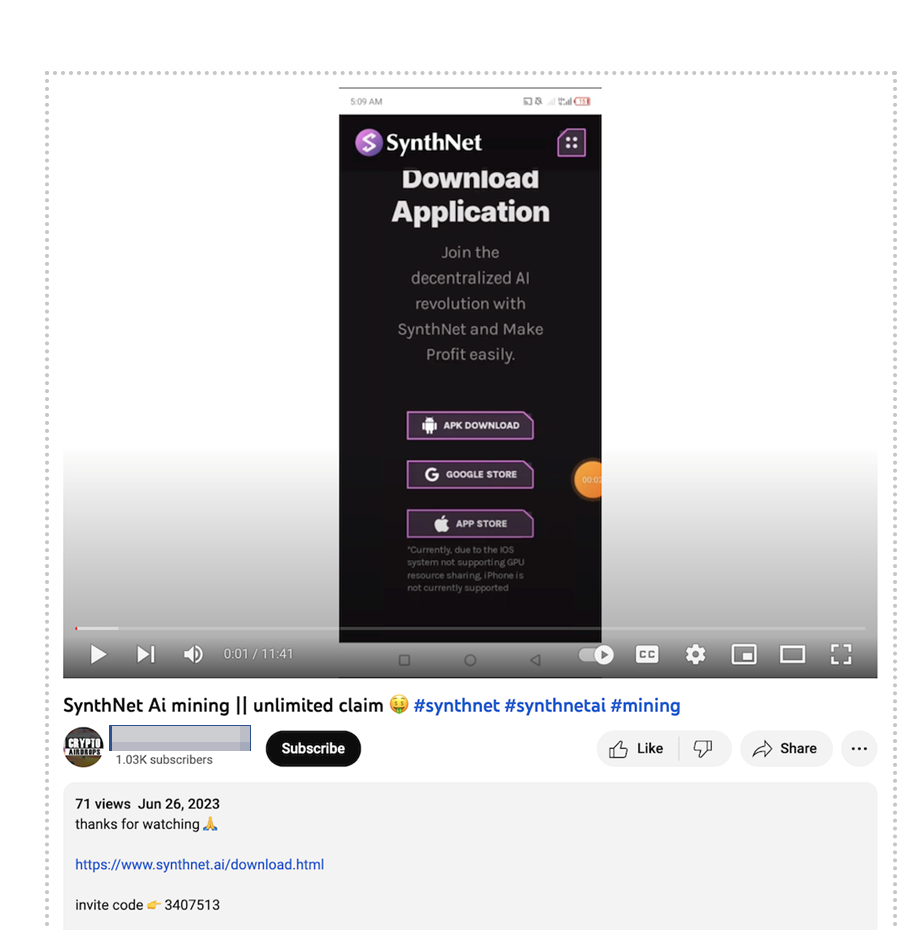
CherryBlos is a highly sophisticated Android malware that targets cryptocurrency users, explicitly seeking to steal their credentials and funds. Distributed through deceptive APK files promoted on social media platforms like Telegram, Twitter, and YouTube, CherryBlos was also found on unauthorized sites promoting money-making scams. Although one of the apps was briefly available on Google Play, it did not contain the malicious CherryBlos payload.
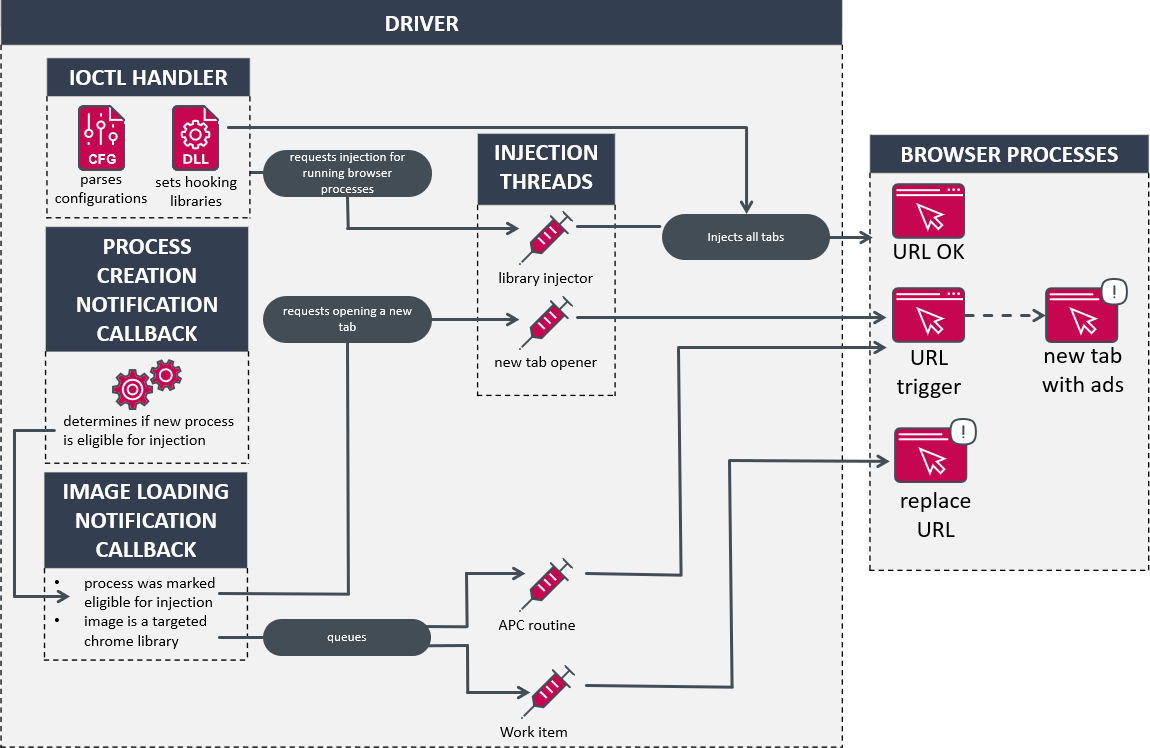
Using a paid version of the Jiagubao commercial software, the developers ensured the malware remained undetected by encrypting the code and code strings. This evasion technique made it challenging for security analysts to uncover its malicious functionality. Additionally, CherryBlos employs methods to bypass restrictions on taking screenshots during sensitive transactions, further enhancing its stealthy operation.
The Unique OCR Technique for Stealing Credentials:
One of the standout features of CherryBlos is its use of optical character recognition (OCR) to extract sensitive information, such as mnemonic passphrases, from images and photos stored on infected devices. Users often store recovery phrases for their cryptocurrency wallets in pictures, and the malware capitalizes on this practice. After translating the images into text using OCR, CherryBlos gains access to the users’ crypto wallets, enabling attackers to steal funds.
Furthermore, CherryBlos acts as a clipboard hijacker for the Binance app, replacing legitimate recipients’ addresses with those controlled by the attackers. As a result, funds sent by users are redirected to the attackers’ wallets, leading to substantial financial losses for victims.
The FakeTrade Campaign: Targeting Unsuspecting Users:
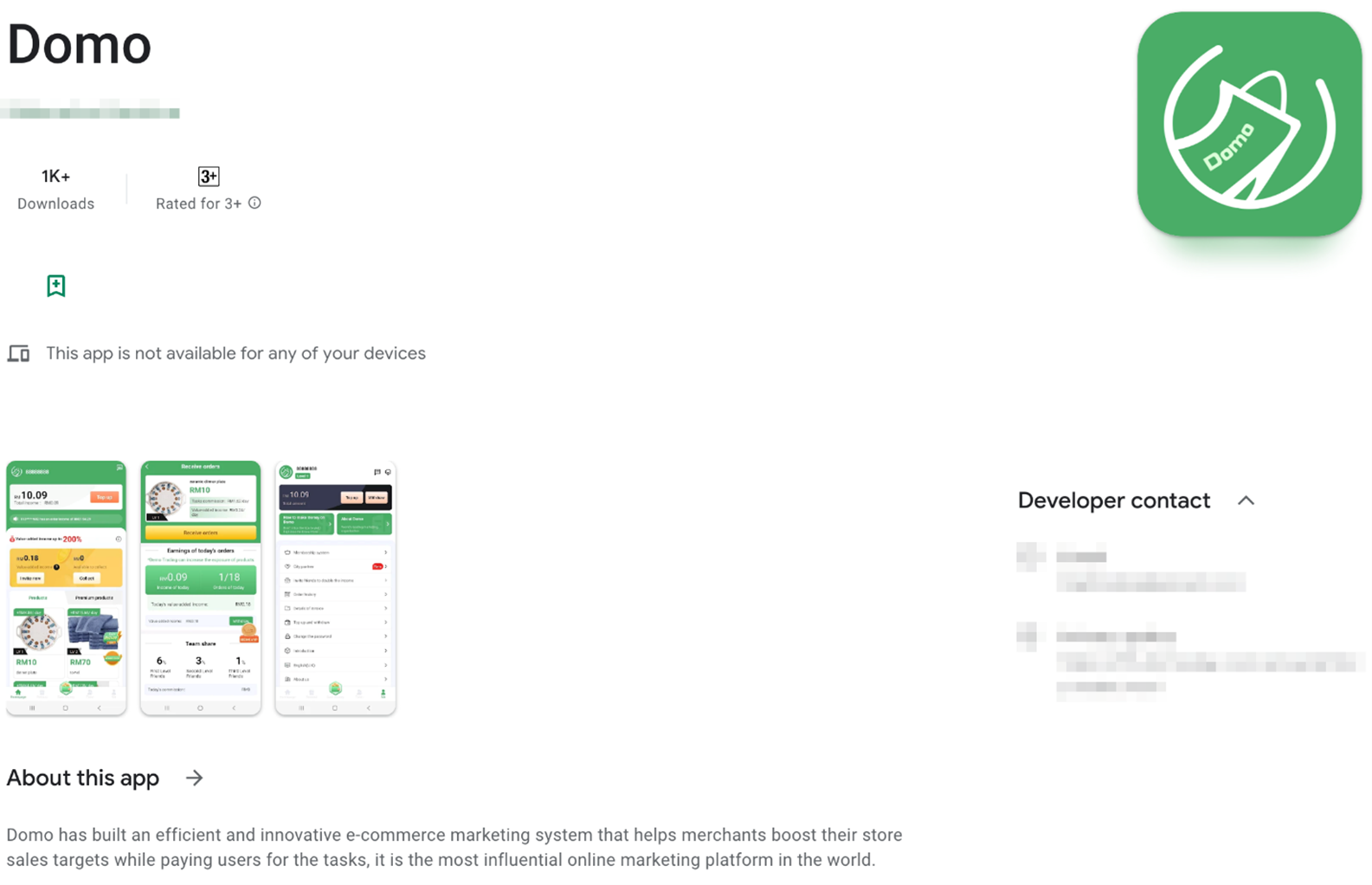
FakeTrade, another malware campaign discovered by Trend Micro, shares network infrastructure and certificates with CherryBlos, indicating the involvement of the same threat actors. This campaign utilizes deceitful methods to lure users, such as phishing sites and shopping-themed apps hosted on Google Play. The 31 scam apps collectively known as FakeTrade entice users into watching ads, agreeing to premium subscriptions, or topping up in-app wallets with virtual rewards. However, victims cannot cash out these rewards, leading to disappointment and financial exploitation.
Google’s Actions and Recommended Measures:
Upon discovering these malicious apps, Google promptly removed them from Google Play. However, manual cleanup may be necessary on infected devices due to the large number of downloads before their removal.
To protect against such threats, users are strongly advised to remain vigilant when downloading apps, especially from unverified sources. Verification of developer information and scrutiny of app reviews can help mitigate potential risks associated with malware distribution.
Conclusion:
The CherryBlos and FakeTrade malware campaigns highlight the ever-evolving cyber threat landscape, with threat actors using sophisticated techniques to target cryptocurrency users and conduct scams. These campaigns serve as a wake-up call for users to prioritize security and exercise caution while downloading apps. Implementing best practices and staying informed about the latest cybersecurity threats can go a long way in safeguarding personal information and financial assets from malicious actors.