In the ever-evolving landscape of cyber threats, a novel and highly sophisticated backdoor malware named ‘Deadglyph’ has emerged, leaving experts baffled and organizations vulnerable. This malware has recently been utilized in a cyber espionage attack against a government agency in the Middle East, shedding light on the capabilities of its creators. Here, we present a comprehensive overview of Deadglyph, its origins, and the group behind it, offering insights drawn from multiple sources.
The Birth of Deadglyph
Deadglyph first came into the spotlight during a cyber espionage operation targeting a government agency in the Middle East. This malware is attributed to the Stealth Falcon APT (Advanced Persistent Threat), also known as Project Raven or FruityArmor. The group, believed to be state-sponsored and operating out of the United Arab Emirates (UAE), has a notorious history of targeting activists, journalists, and dissidents, dating back nearly a decade.
A Complex Loading Chain
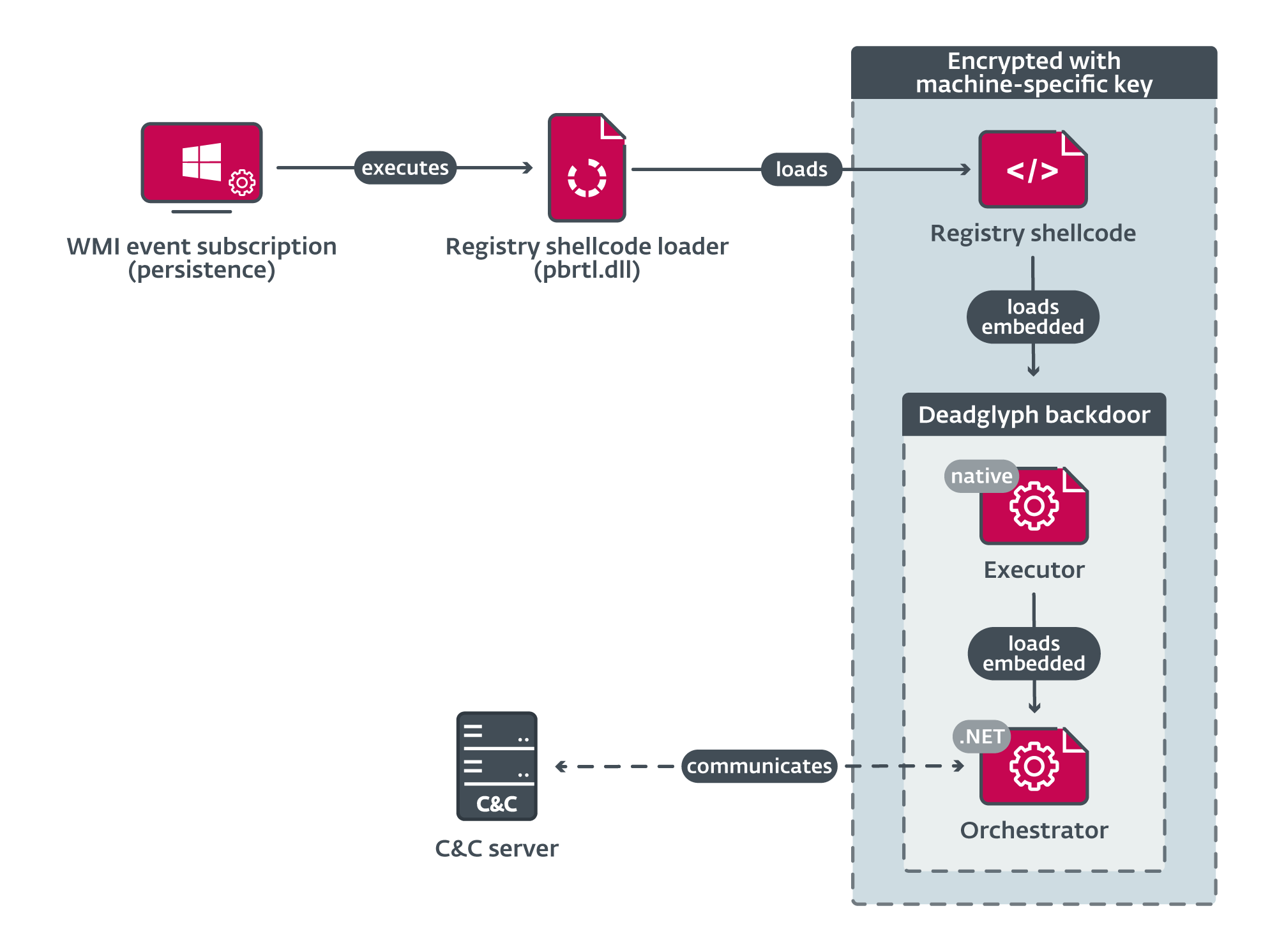
ESET researchers have provided a detailed analysis of Deadglyph’s modus operandi. Although the means of initial infection remain unclear, it is suspected that a malicious executable, possibly a program installer, serves as the point of entry. Once inside a target system, Deadglyph deploys a complex loading chain designed to evade detection.
The loading chain begins with a registry shellcode loader (DLL) that extracts code from the Windows registry to initiate the Executor (x64) component. This Executor, in turn, is responsible for loading the Orchestrator (.NET) component. Notably, only the initial component exists as a DLL file on the compromised system’s disk, minimizing the likelihood of detection.
An ingenious evasion tactic employed by Deadglyph involves a homoglyph attack. The attackers mimic Microsoft Corporation in the VERSIONINFO resource, using distinct Unicode characters that appear visually similar but are not identical to the original characters. This obfuscation technique adds an extra layer of complexity for security analysts attempting to uncover the malicious code.
Modular Design for Enhanced Flexibility
Deadglyph’s modular design sets it apart from many other malware strains. Instead of embedding a predefined set of commands, this malware fetches its instructions dynamically from a command and control (C&C) server in the form of additional modules. This modular approach grants the threat actors unparalleled flexibility to adapt and tailor their attacks to specific targets.
While the full extent of Deadglyph’s capabilities remains shrouded in mystery, ESET believes that there are nine to fourteen different modules. However, they could only obtain three of them: a process creator, an information collector, and a file reader.
The information collector relies on Windows Management Instrumentation (WMI) queries to provide the Orchestrator with a wealth of information about the compromised system, including details about the operating system, network adapters, installed software, drives, services, users, and security software.
The process creator is a command execution tool, executing specified commands as new processes and reporting the results to the Orchestrator.
The file reader module reads the content of files and offers the option to delete them after retrieval, potentially allowing threat actors to cover their tracks effectively.
A Formidable Threat with Unknown Origins
While Deadglyph’s capabilities are indeed formidable, one crucial aspect remains uncertain: the method of initial infection. Without a clear understanding of how this malware infiltrates systems, devising specific defense strategies is challenging.
For now, organizations can rely on the Indicators of Compromise (IoCs) provided in the ESET report to bolster their defenses against this emerging cyber threat. Vigilance and proactive security measures are crucial in the ongoing battle against cyber espionage and sophisticated APTs like Deadglyph.