BlackCat Ransomware Group Exploits WinSCP Application in Malvertising Campaign

Recently, cyber attackers have become increasingly proficient at exploiting unknown vulnerabilities and deploying innovative tactics that organizations may not anticipate. One such alarming case involves the BlackCat ransomware group, ALPHV. They have been found to operate malicious advertising (malvertising) campaigns to distribute malware via fake webpages mimicking the popular WinSCP file-transfer application for Windows. By gaining initial access through this deceptive technique, the threat actors target valuable corporate networks, including system administrators, web admins, and IT professionals. This ransomware infection vector was discovered by analysts at Trend Micro.
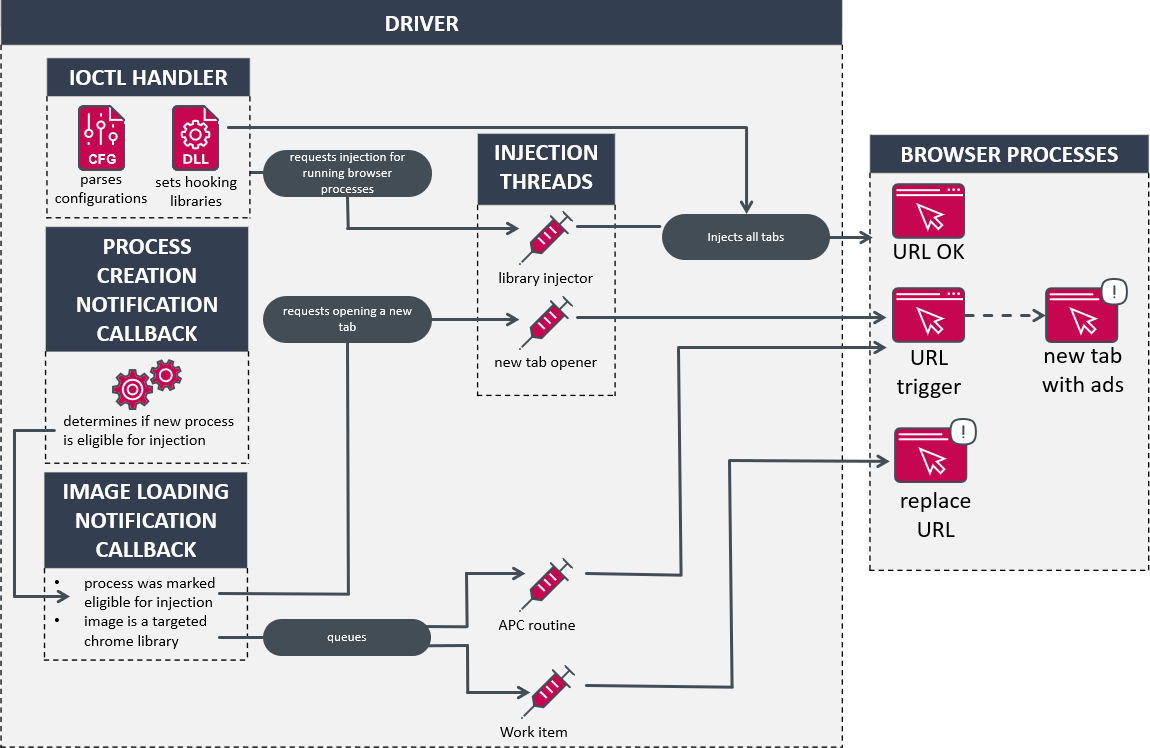
The Attack Chain:
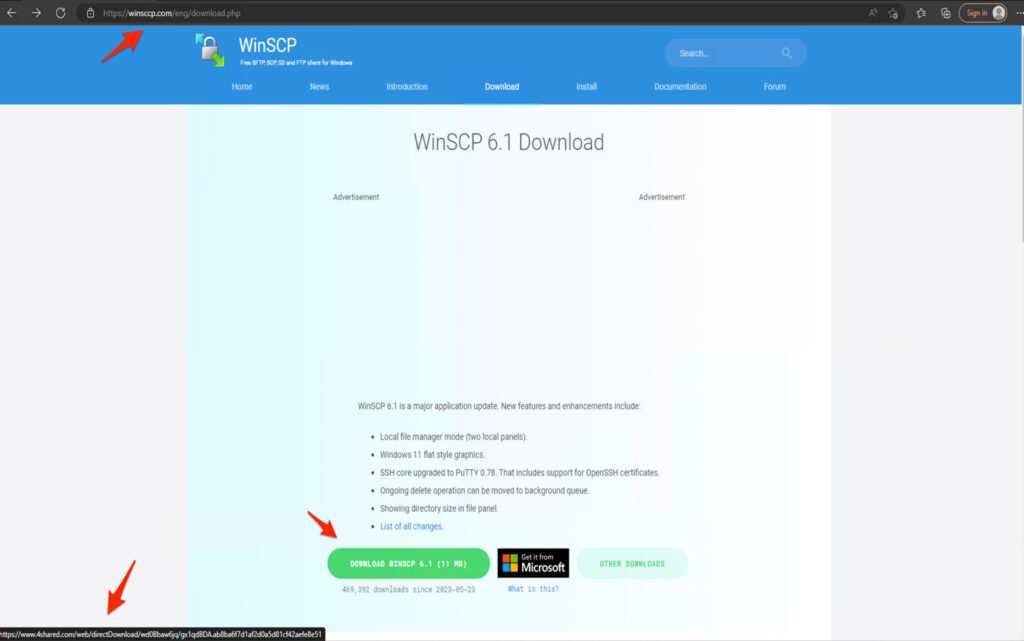
The insidious attack orchestrated by the BlackCat ransomware group begins with users searching for “WinSCP Download” on major search engines like Bing or Google. However, instead of legitimate download sites, the malvertising campaign manipulates search results to promote malicious ads ranked above genuine ones. When unsuspecting victims click on these ads, they are directed to seemingly harmless websites offering tutorials on automating WinSCP file transfers.
Clone Websites and Malicious Payload:
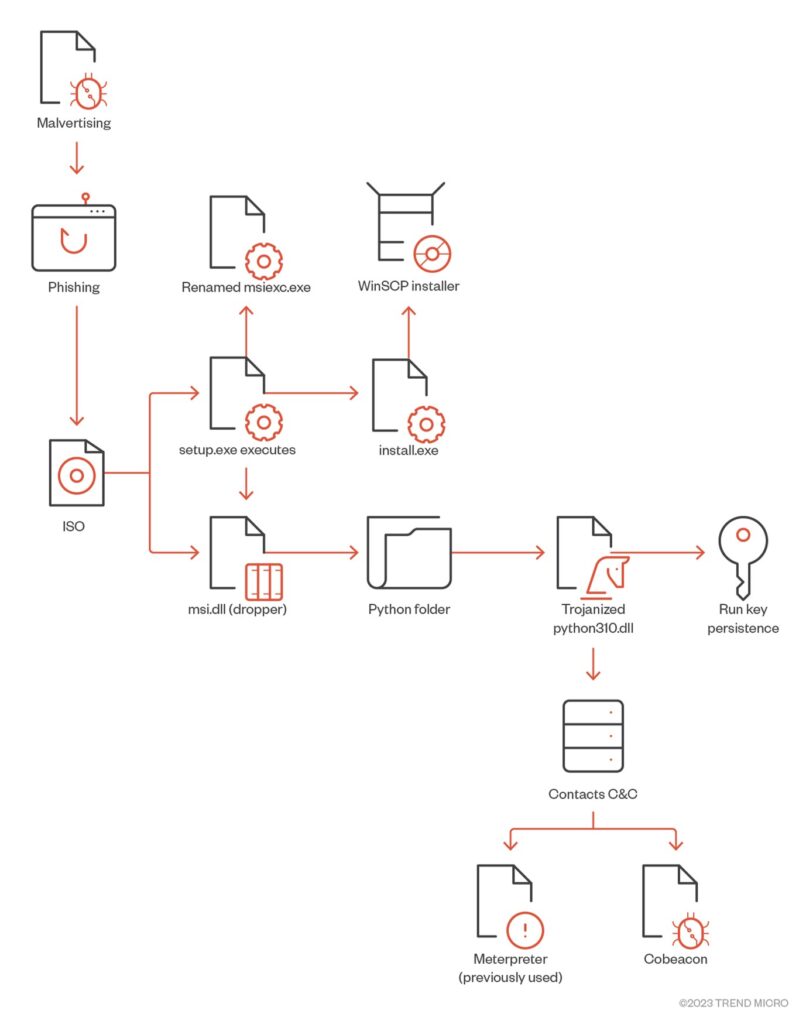
These tutorial websites, carefully designed to evade detection, serve as intermediaries to redirect users to cloned web pages that closely resemble the official WinSCP website. The cloned pages feature a deceptive “Download” button, and when clicked, the victim unwittingly downloads an ISO file containing the malware dropper, “setup.exe,” and the payload, “msi.dll.”
Establishing Persistence and Cobalt Strike Beacon:
When the victim executes “setup.exe,” it triggers the execution of “msi.dll,” which extracts a Python folder from the DLL RCDATA section, masquerading as a genuine WinSCP installer. Furthermore, the malware installs a trojanized “python310.dll” and establishes persistence by creating a run key named “Python” with the value “C:\Users\Public\Music\python\pythonw.exe.” Subsequently, the executable “pythonw.exe” loads an obfuscated “python310.dll” containing a Cobalt Strike beacon that connects to a command-and-control server, enabling the threat actors to maintain control over the compromised system.
Tools Leveraged by ALPHV:
The BlackCat ransomware group deploys various tools to deepen their compromise of the targeted network. These tools include:
AdFind: A command-line tool retrieves Active Directory (AD) information.
PowerShell scripts: Employed for gathering user data, extracting ZIP files, and executing various scripts.
AccessChk64: A command-line tool used for user and group permission reconnaissance.
Findstr: A command-line tool used to search for passwords within XML files.
PowerView: A PowerSploit script utilized for AD reconnaissance and enumeration.
Python scripts: Executing the LaZagne password recovery tool and obtaining Veeam credentials.
PsExec, BitsAdmin, and Curl: Utilized for lateral movement across the network.
AnyDesk: A legitimate remote management tool abused for maintaining persistence.
KillAV BAT script: Attempting to disable or bypass antivirus and antimalware programs (unsuccessful due to robust protections).
PuTTY Secure Copy client: Employed for exfiltrating collected information from the compromised system.
Conclusion and Recommendations:
The BlackCat ransomware group’s sophisticated and deceptive attack strategy highlights the need for organizations to prioritize early detection and rapid response within their networks. By understanding the intricacies of attack scenarios, organizations can identify potential vulnerabilities and implement necessary preventive measures.