Rustbucket Malware Evolves with Enhanced Persistence and Evasion Techniques
In recent reports, security researchers have unveiled an updated version of the Rustbucket malware, a sophisticated threat targeting macOS systems. This variant, attributed to the North Korean threat actor BlueNoroff, exhibits new persistence capabilities and utilizes dynamic network infrastructure to evade detection and enhance its command-and-control (C2) capabilities. The malware, discovered by Elastic Security Labs, sheds light on the evolving tactics employed by the DPRK’s cyber campaign..
Enhanced Persistence Mechanisms:
The latest Rustbucket variant demonstrates an unprecedented persistence mechanism, enabling it to remain undetected for an extended period. By deploying a plist file at the path /Users/
Dynamic Network Infrastructure for Command and Control:
The Rustbucket malware employs a dynamic network infrastructure methodology for command and control to facilitate its malicious operations. By leveraging dynamic DNS domains such as docsend.linkpc[.]net, the malware establishes communication channels with its C2 server while evading traditional detection mechanisms. This technique poses a significant challenge for cybersecurity professionals aiming to track and neutralize the malware’s activities effectively.
Targeted Cyber Operations by BlueNoroff:
The Rustbucket malware, attributed to the BlueNoroff group, is part of the larger Lazarus Group intrusion set. Supervised by the Reconnaissance General Bureau (RGB), North Korea’s primary intelligence agency, BlueNoroff is known for its advanced cyber capabilities. This recent development marks the first instance of BlueNoroff specifically targeting macOS systems, indicating an expansion of their victimology and cross-platform malware development efforts.
Infection Chain and Initial Intrusion Vector:
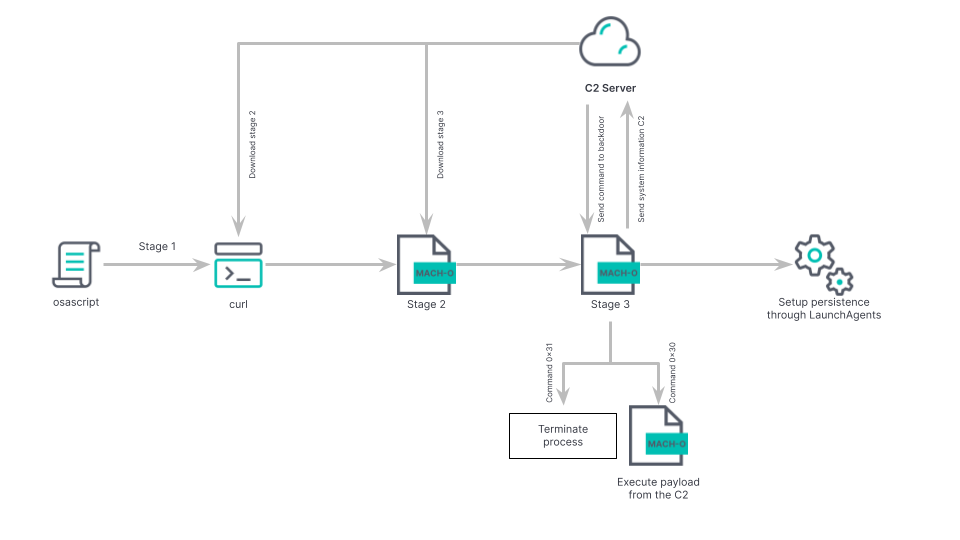
The infection chain of Rustbucket involves a macOS installer file that deploys a backdoored PDF reader capable of executing malicious activities. Notably, the malware only triggers its malicious actions when a weaponized PDF file is launched using the rogue PDF reader. BlueNoroff utilizes phishing emails and fictitious personas on social networks like LinkedIn as initial intrusion vectors. The campaign focuses primarily on finance-related institutions in Asia, Europe, and the United States, suggesting an intention to generate illicit revenue and evade sanctions.
Advanced Capabilities and Malware Behavior:
The Rustbucket malware exhibits advanced capabilities, making detection and prevention challenging. It employs various macOS APIs for operations such as gathering comprehensive system information, including the computer name, active processes, timestamps, and system boot time. The malware communicates with the C2 server by transmitting gathered data via a POST request, using a User-Agent string formatted as Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0).
Future Implications and Mitigation Efforts:
The evolution of Rustbucket showcases the constant innovation and adaptability of North Korean threat actors. As they expand their capabilities and target different platforms, it becomes crucial for cybersecurity professionals and organizations to remain vigilant and implement robust security measures. Proactive threat intelligence, network monitoring, user awareness training, and the adoption of advanced endpoint protection solutions can help mitigate the risks associated with this evolving threat landscape.
Conclusion:
The DPRK’s cyber campaign, spearheaded by the BlueNoroff group, continues to evolve with the emergence of an updated variant of the Rustbucket malware. With enhanced persistence mechanisms and dynamic network infrastructure for command and control, the malware poses a significant challenge to detection and prevention efforts. It is imperative for organizations and security professionals to stay informed about the evolving tactics employed by threat actors and take proactive measures to safeguard their systems and data from sophisticated cyber threats.