Proxyjacking: A Stealthy Threat Exploiting Bandwidth for Profit

In the rapidly evolving world of cyber threats, attackers are constantly finding new ways to maximize their gains with minimal effort. One such technique is proxyjacking, a method that has recently gained popularity among cybercriminals. This article aims to shed light on this emerging threat and provide insights into a proxyjacking campaign recently discovered by the Akamai Security Intelligence Response Team (SIRT).
What is Proxyjacking?
While many people are familiar with cryptojacking, where attackers steal resources for cryptocurrency mining, proxyjacking takes it a step further. In proxyjacking, attackers not only steal resources but also exploit the victim’s unused bandwidth. They secretly turn the victim’s system into a peer-to-peer (P2P) proxy node and then monetize it through various proxy networks, such as Peer2Proxy or Honeygain.
The Value of Proxies for Cybercriminals:
Proxies provide cybercriminals with the ability to hide their tracks and make it extremely difficult to trace their activities. By routing malicious traffic through multiple peer nodes, they can obfuscate their actions and avoid detection. This makes proxies highly valuable to threat actors engaging in illicit activities.
The Proxyjacking Campaign:
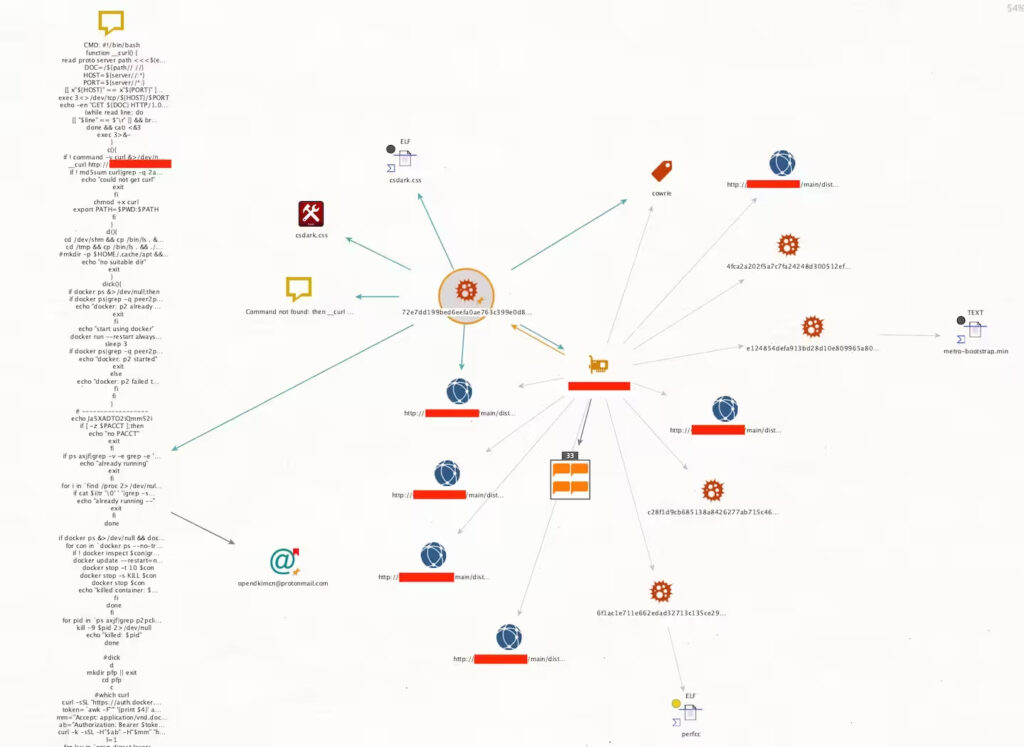
Akamai SIRT uncovered an active proxyjacking campaign that leverages SSH for remote access. Attackers use malicious scripts to enlist victim servers into P2P proxy networks, enabling them to monetize the victim’s extra bandwidth. The campaign is designed to operate stealthily, minimizing the chances of discovery.
How Proxyjacking Exploits Legitimate Services:
Proxyjacking for profit involves using legitimate companies like Peer2Profit and Honeygain, which allow users to share their unused bandwidth for monetary compensation. However, these companies often fail to properly vet the sourced proxy nodes, leading to the exploitation of unsuspecting users. The seemingly harmless act of sharing bandwidth turns into cybercrime when deployed without user consent, allowing attackers to amplify their earnings at the victims’ expense.
The Attack Methodology:
The discovered campaign involves attackers establishing SSH connections to compromised systems, encoding Bash scripts to obfuscate their true functionality, and enlisting victim systems into proxy networks. The attackers use Docker containers to run resource-sharing programs and remove competing instances. The campaign employs various techniques to evade detection and operate undetected.
Mitigating Proxyjacking:
To defend against proxyjacking, it is essential to implement strong security fundamentals. Regular users should use complex passwords, store them securely in a password manager, apply application patches promptly, and enable multi-factor authentication whenever possible. Deeper knowledge of computer security allows vigilant monitoring of running containers, network traffic anomalies, and regular vulnerability scans.
In case of an attack, affected individuals should investigate the intrusion, clean up the system, change all passwords, ensure the software is up-to-date, and consider implementing a stricter security policy. Engaging professional incident response services may be necessary for sensitive systems or those containing valuable data.
The Growing Threat Landscape:
Proxyjacking joins the ranks of other criminal schemes that exploit compromised devices for financial gain. Similar to cryptojacking and spamming, legitimate services are abused for malicious purposes. Proxyjacking poses a significant challenge as it minimizes CPU usage and evades traditional detection methods. Layer 7 attacks facilitated through proxy networks further exacerbate the problem.
Conclusion:
Proxyjacking represents a new and concerning cyber threat that exploits unused bandwidth for profit. Cybercriminals leverage legitimate services and compromised systems to amplify their earnings. Defending against proxyjacking requires a combination of strong security measures and proactive monitoring. As the threat landscape continues to evolve, it is crucial for individuals and organizations to stay vigilant and implement robust cybersecurity practices to mitigate the risks of proxyjacking.