In a recent cybersecurity development, hackers launched a sophisticated phishing campaign that exploited a zero-day vulnerability in Salesforce’s email services and SMTP servers. This campaign targeted valuable Facebook accounts by exploiting a flaw known as “PhishForce” to bypass sender verification safeguards in Salesforce and leverage quirks in Facebook’s web games platform to mass-send phishing emails. The attackers could distribute malicious emails through Salesforce, evading secure email gateways and filtering rules, ultimately reaching the target’s inbox undetected. The campaign was discovered by Guardio Labs analysts Oleg Zaytsev and Nati Tal.
The Sophisticated Phishing Campaign
The attackers successfully exploited Salesforce’s “Email-to-Case” feature to convert incoming customer emails to actionable tickets for support teams. By setting up a new “Email-to-Case” flow, they gained control of a Salesforce-generated email address and created a new inbound email address on the “salesforce.com” domain. Subsequently, they designated this address as an “Organization-Wide Email Address,” which Salesforce’s Mass Mailer Gateway uses for outbound emails. The attackers confirmed domain ownership through the verification process, allowing them to send phishing emails using their Salesforce email address without being detected by verification protections or email filters.
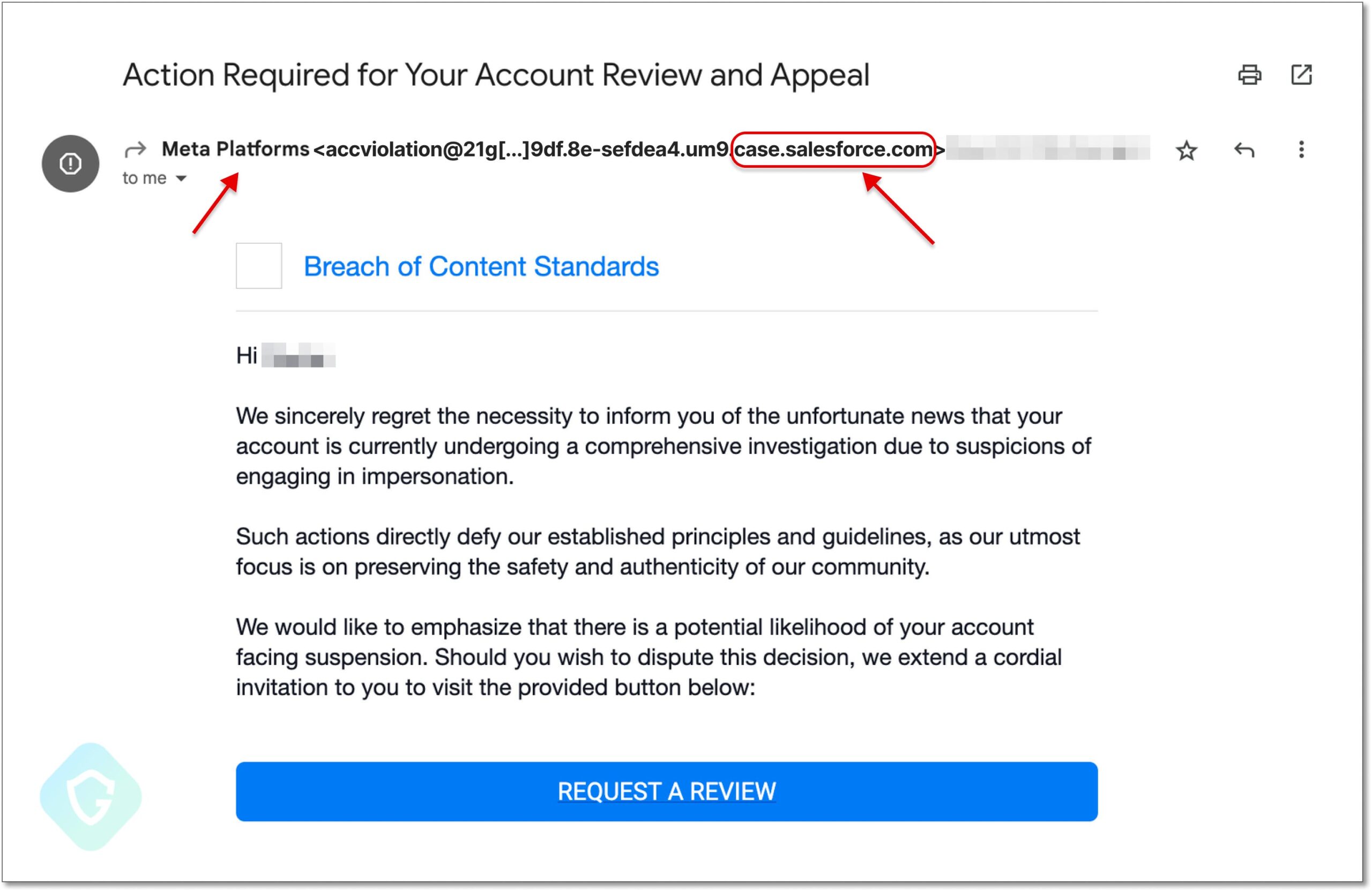
The phishing emails masqueraded as coming from Meta (previously Facebook’s parent company), using the “case.salesforce.com” domain, which added legitimacy to the attack and made it harder for email recipients to identify the fraud. The emails sought to trick recipients into clicking on a link by claiming that their Facebook accounts were under investigation for suspicions of impersonation.
The Rogue Landing Page
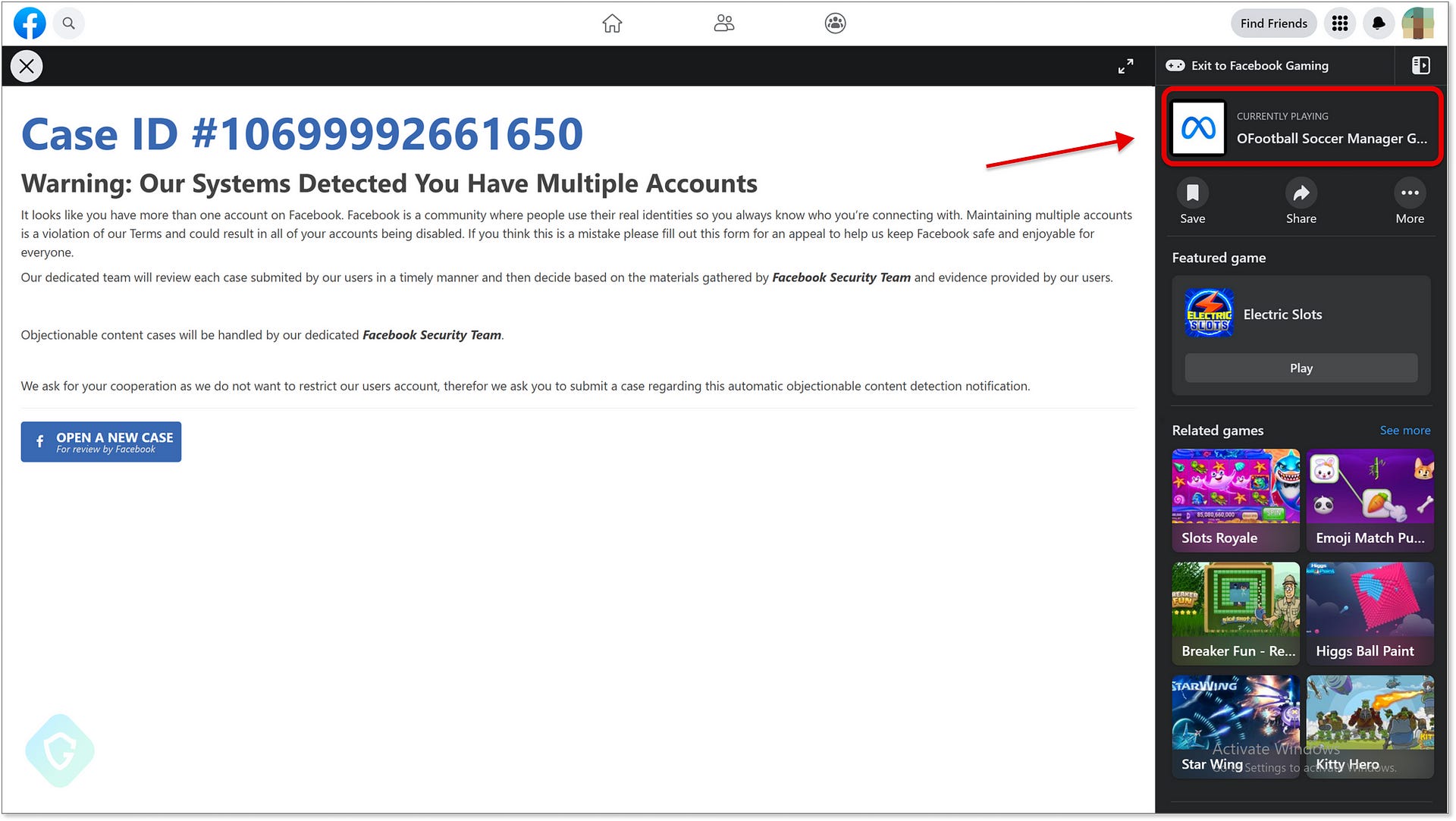
Upon clicking the embedded link in the phishing email, victims were directed to a rogue landing page hosted on the Facebook gaming platform under “apps.facebook.com.” The phishing kit hosted on this platform aimed to steal Facebook account credentials, including two-factor authentication bypassing mechanisms, further complicating the detection process for traditional anti-spam and anti-phishing mechanisms.
Collaborative Mitigation Efforts
Guardio Labs analysts Oleg Zaytsev and Nati Tal detected and reported the campaign. They promptly notified Salesforce and collaborated with them throughout the remediation process. Salesforce confirmed the vulnerability and successfully addressed it a month later, implementing new checks to prevent using email addresses from the “@salesforce.com” domain for such malicious activities.
Facebook’s Role
Regarding the abuse of “apps.facebook.com,” Guardio Labs noted that Facebook retired this platform in July 2020, making it seemingly impossible for attackers to create the game canvas used in the phishing attack. However, legacy accounts that used the platform before its deprecation still had access, and threat actors might be acquiring such accounts on the dark web, facilitating this attack.
Implications and Recommendations
This sophisticated phishing campaign highlights the growing sophistication of cyber threats targeting seemingly legitimate services to carry out malicious activities. As phishing actors continuously explore potential abuse opportunities on reputable service providers, novel security gaps emerge, posing severe user risks. Traditional email protection solutions may prove insufficient to thwart such attacks. Therefore, users are urged to exercise caution and scrutinize every email that arrives in their inbox, looking for inconsistencies and verifying the claims made in those messages.
Conclusion
The collaboration between Guardio Labs, Salesforce, and Facebook’s Meta during the mitigation process exemplifies the importance of coordinated efforts to combat cyber threats. This incident reminds organizations and individuals alike to remain vigilant, keep security systems up to date, and exercise caution in dealing with suspicious emails to protect against sophisticated phishing campaigns and other cyber threats.