Chinese Threat Actor Targeting European Government Entities Using HTML Smuggling Technique
A Chinese threat actor has recently been identified by Check Point Research (CPR) for targeting Foreign Affairs ministries and embassies in Europe. The campaign, known as SmugX, has been active since at least December 2022. The attackers employ HTML smuggling techniques to deliver the PlugX remote access trojan, enabling them to evade network-based detection measures. This article will provide an overview of the SmugX campaign, its infection chains, and the tactics used by the threat actor.
HTML Smuggling: An Overview:
HTML Smuggling is a well-documented technique utilized by cyber criminals and state-sponsored actors. It involves embedding malicious files within HTML documents, allowing them to bypass network-based detection measures. In the SmugX campaign, the attackers utilize HTML Smuggling to download JavaScript or ZIP files. When users open the malicious HTML documents, the embedded payload is decoded and saved to a JavaScript blob, which is then dynamically created as a URL object. The code initiates a simulated user click action, resulting in the download of the malicious file.
Focus on European Governmental Entities:
The lure themes in the SmugX campaign primarily focus on European domestic and foreign policies, explicitly targeting governmental ministries in Eastern Europe. The documents used as lures include content related to diplomatic affairs, including China. The filenames of the archived files also suggest that the intended victims were diplomats and government entities.
Gathering Information:
The threat actors employed a reconnaissance technique known as pixel tracking. By embedding an invisible tracking pixel in a document named “China Tries to Block Prominent Uyghur Speaker at UN.docx,” the attackers collected information about the recipient’s behavior, such as the time and location of document access.
Infection Chains:
The SmugX campaign utilizes two leading infection chains. In the first scenario, the HTML file smuggles a ZIP archive containing a malicious LNK file. This LNK file runs PowerShell, which extracts a compressed archive embedded within it. The extracted files include a legitimate executable, a malicious sideloaded DLL, and the PlugX payload. In the second scenario, the HTML smuggling technique is used to download a JavaScript file, which then downloads and executes an MSI file from the attackers’ server. The MSI file drops three files: a legitimate executable, a loader DLL, and the encrypted PlugX payload.
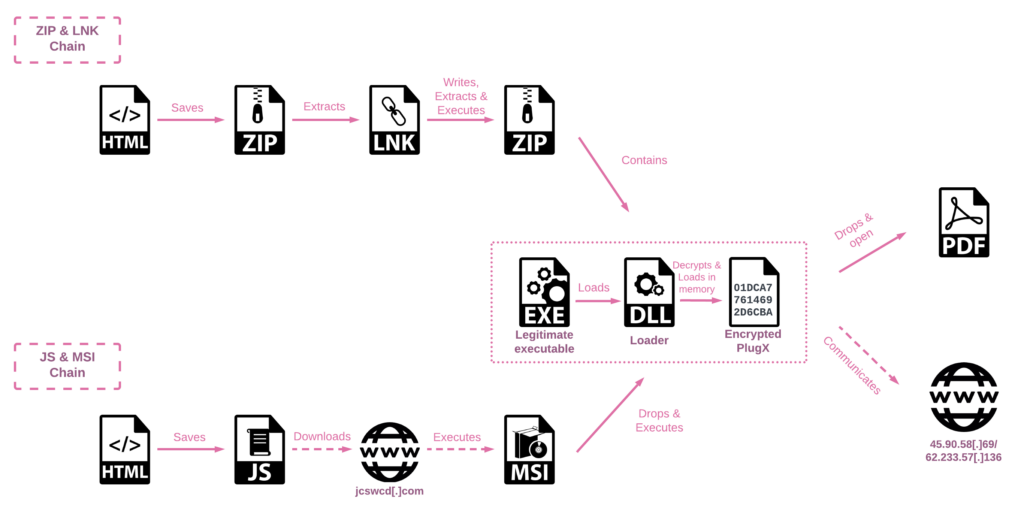
How SmugX Spreads:
The final payload delivered by the SmugX campaign is the PlugX malware, a remote access trojan widely associated with Chinese threat actors since 2008. PlugX operates as a modular tool, allowing attackers to carry out various malicious activities on compromised systems, such as file theft, screen captures, keystroke logging, and command execution. To ensure persistence, the malware copies legitimate programs and DLLs to hidden directories and adds the legitimate program to the Run registry key.
Attribution:
While the identity of the threat actor behind the SmugX campaign remains unclear, similarities exist between this activity and previously reported campaigns attributed to Chinese threat actors like Mustang Panda and RedDelta. However, insufficient evidence exists to conclusively attribute the SmugX campaign to a specific group.
Conclusion:
The SmugX campaign demonstrates a shift by Chinese threat actors towards targeting European government entities. The attackers have been able to evade detection and maintain a low profile by employing HTML smuggling techniques. The PlugX malware used in the campaign allows the threat actors to conduct various malicious activities on compromised systems. Check Point Software customers remain protected against this threat through their Threat Emulation and Harmony Endpoint solutions.