In a recent cybersecurity revelation, Check Point researchers have uncovered an active and evolving malware campaign that poses a severe threat to banking customers in Latin America. This campaign centers around the notorious BBTok banking trojan, which, since its initial discovery in 2020, has displayed a remarkable ability to adapt and refine its tactics to target users primarily in Brazil and Mexico.
The BBTok Banking Trojan
The malware at the heart of this campaign is the BBTok banking trojan, which first surfaced in Latin America in 2020. This trojan stands out for its ability to mimic the interfaces of over 40 major banks in Mexico and Brazil, including well-known names such as Citibank, Scotiabank, Banco Itaú, and HSBC. Its primary aim is to deceive victims into providing their two-factor authentication (2FA) codes and payment card details.
An Evolving Threat Landscape
The BBTok campaign has shown a remarkable capacity for evolution over time, adapting its tactics and techniques to evade detection and increase its effectiveness. Since its initial appearance, the operators have been refining their strategies to improve the trojan’s obfuscation, diversify infection chains, and add new layers of sophistication.
Infection Chains and Final Payload
The infection process culminates in two variations: one for Windows 7 and another for Windows 10. These versions differ slightly in response to newly implemented detection mechanisms.
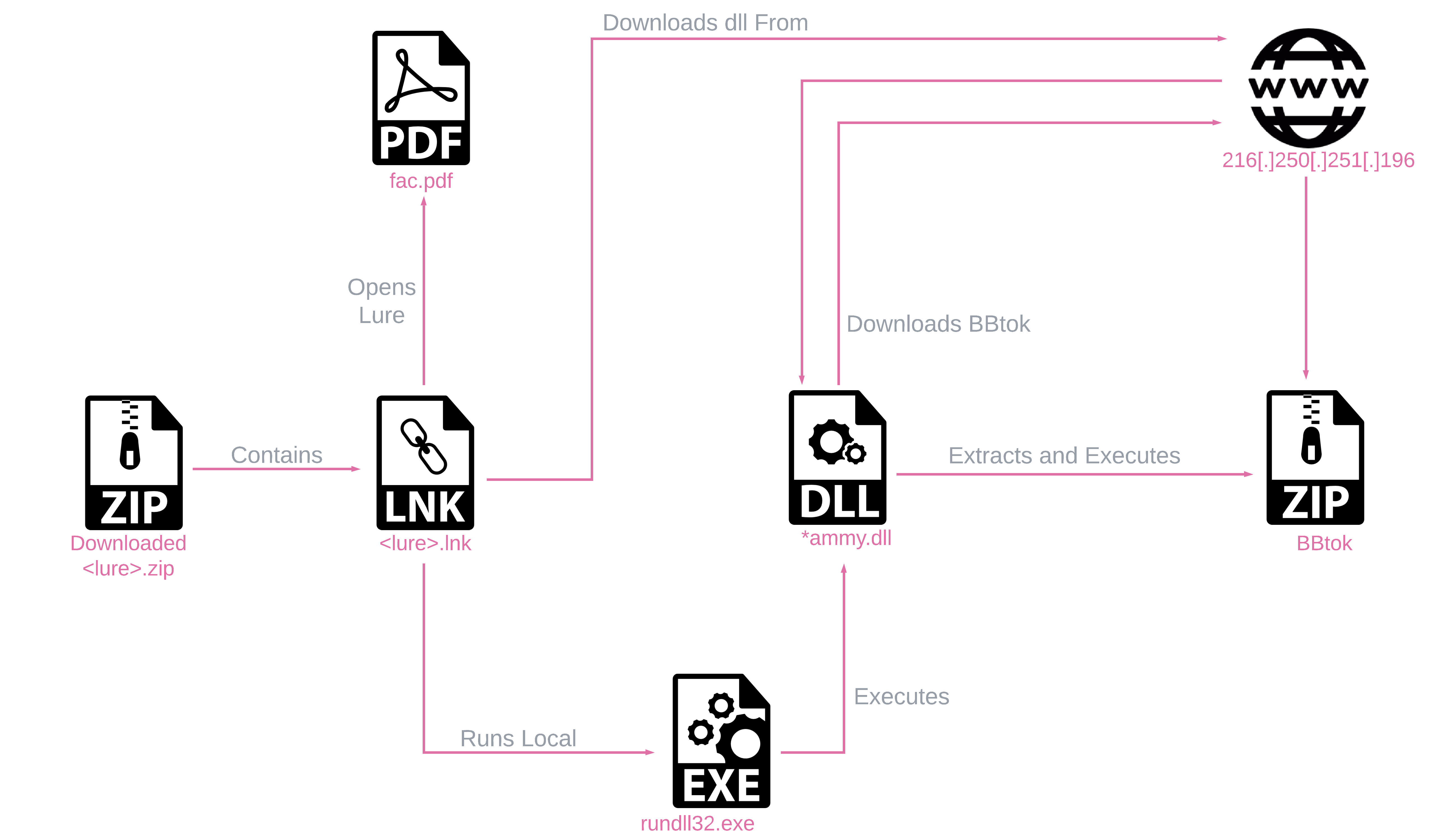
Windows 7 Infection Chain
The Windows 7 infection chain revolves around an LNK file stored within a ZIP archive. Upon execution, the LNK file activates the *ammy.dll payload via rundll32.exe, ultimately leading to the deployment of the BBTok payload.
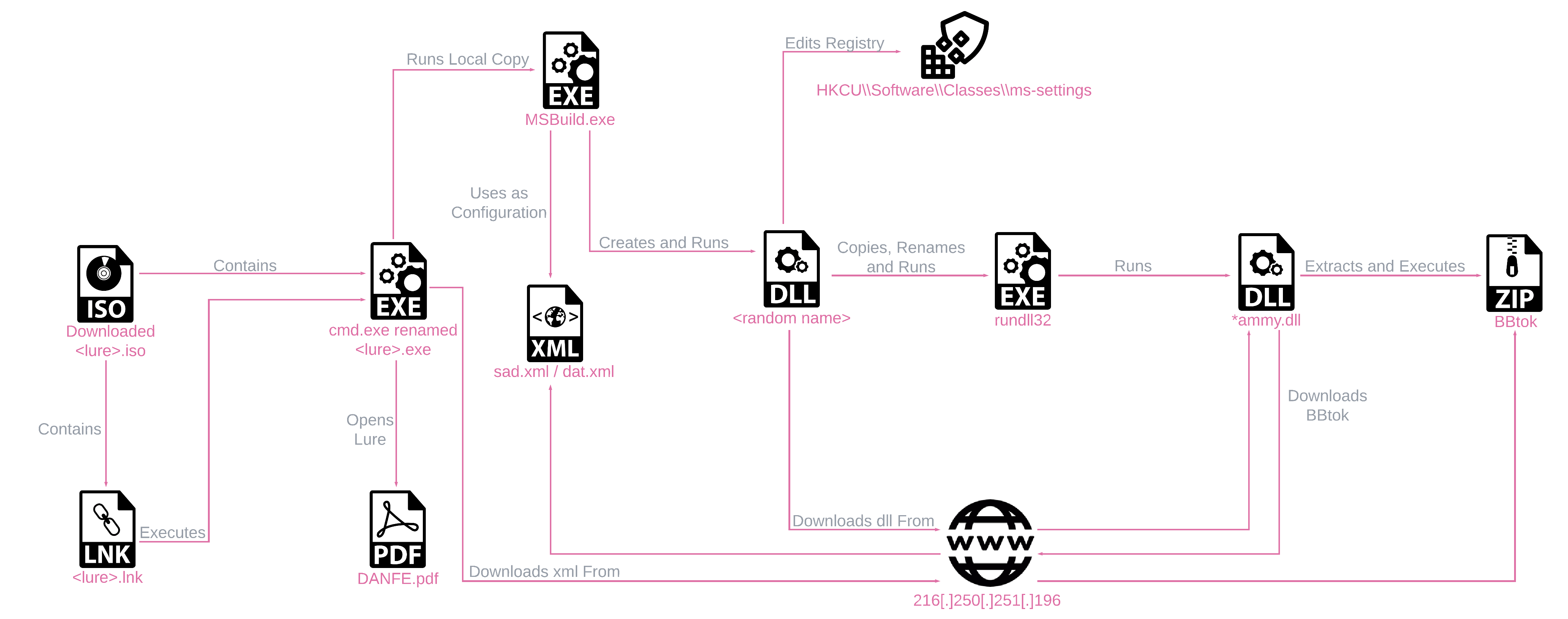
Windows 10 Infection Chain
The Windows 10 infection chain is stored in an ISO file, comprising an LNK file, a lure file, and a renamed cmd.exe executable. Clicking the LNK file triggers the infection chain, which uses the renamed cmd.exe to execute a series of commands, ultimately downloading and executing the BBTok payload.
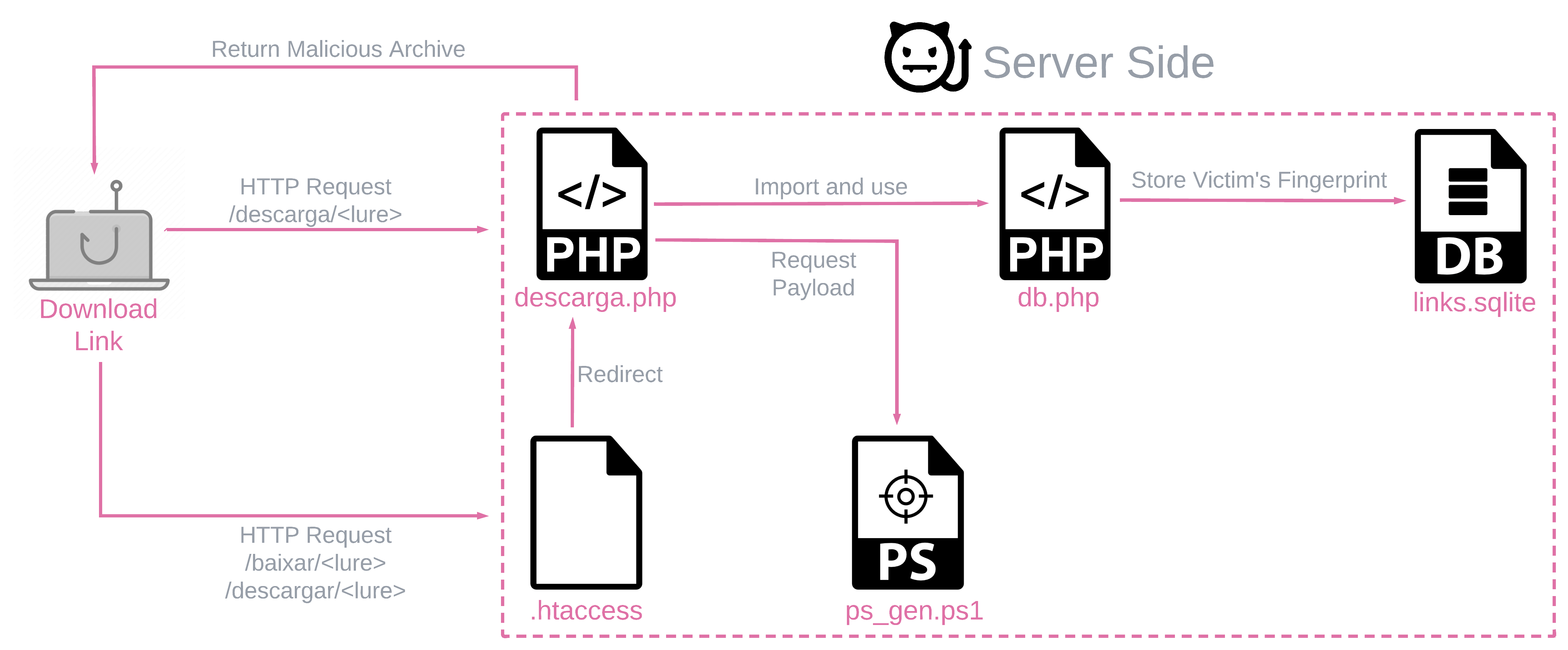
Server-Side Components and Payload Generation
The attackers have also invested in server-side components responsible for distributing the malware. These components are involved in serving malicious payloads likely distributed through phishing links. Researchers have observed numerous iterations of server-side scripts and configuration files, indicating the campaign’s ongoing evolution.
Obfuscation Techniques
All payloads undergo obfuscation via the Add-PoshObfuscation function, obscuring their true nature and intent.
Targeted Geofencing and Custom Payloads
The BBTok campaign employs geofencing checks to ensure that victims are exclusively from Brazil or Mexico, heightening the malware’s effectiveness. Additionally, payloads are uniquely generated for each victim based on their operating system and location, making it more challenging to detect and combat.
The Operator’s Cautious Approach
One distinctive characteristic of this campaign is the operators’ cautious approach. All banking activities are executed only upon direct command from the command-and-control (C2) server and are not automatically carried out on every infected system. This level of control suggests a high degree of sophistication on the part of the threat actors.
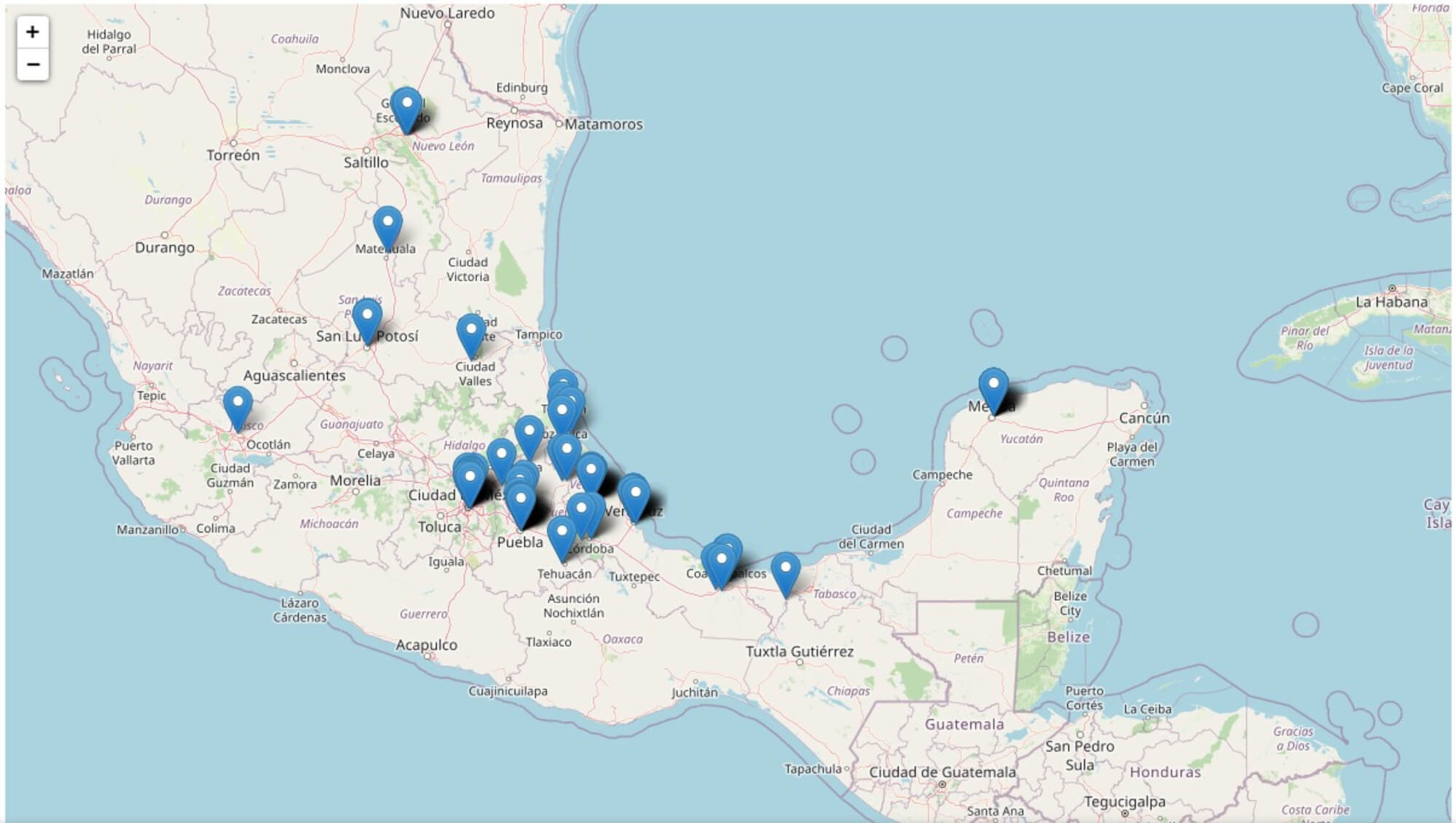
Victimology and Attribution
An analysis of server-side components has also provided insight into the campaign’s victimology. A database of over 150 unique entries indicates that the threat actors have achieved a degree of success in infecting targets. The presence of Portuguese language in the source code and phishing emails points to the likely origin of the attackers, with strong indicators suggesting they operate from Brazil.
Conclusion
In conclusion, the BBTok banking trojan campaign poses a significant and evolving threat to banking customers in Latin America, particularly in Brazil and Mexico. Despite its relatively low profile, this trojan continues to be actively deployed, and its unique delivery method involving various file types, geofencing, and obfuscation techniques makes it a persistent danger to individuals and organizations in the region.
This campaign’s ability to adapt and refine its tactics underscores the importance of ongoing vigilance and cybersecurity measures to protect against evolving threats in the financial sector. Security researchers and organizations must remain proactive in countering these threats to safeguard sensitive financial information and prevent account takeovers.

