In the ever-evolving landscape of cybersecurity threats, a new adversary, AtlasCross, has emerged on the scene and raised significant concerns among cybersecurity experts. This advanced persistent threat (APT) group, recently brought to the forefront by NSFOCUS Security Labs, is known for its sophisticated tactics, careful approach, and a series of targeted attacks.
Red Cross-themed Phishing Lures
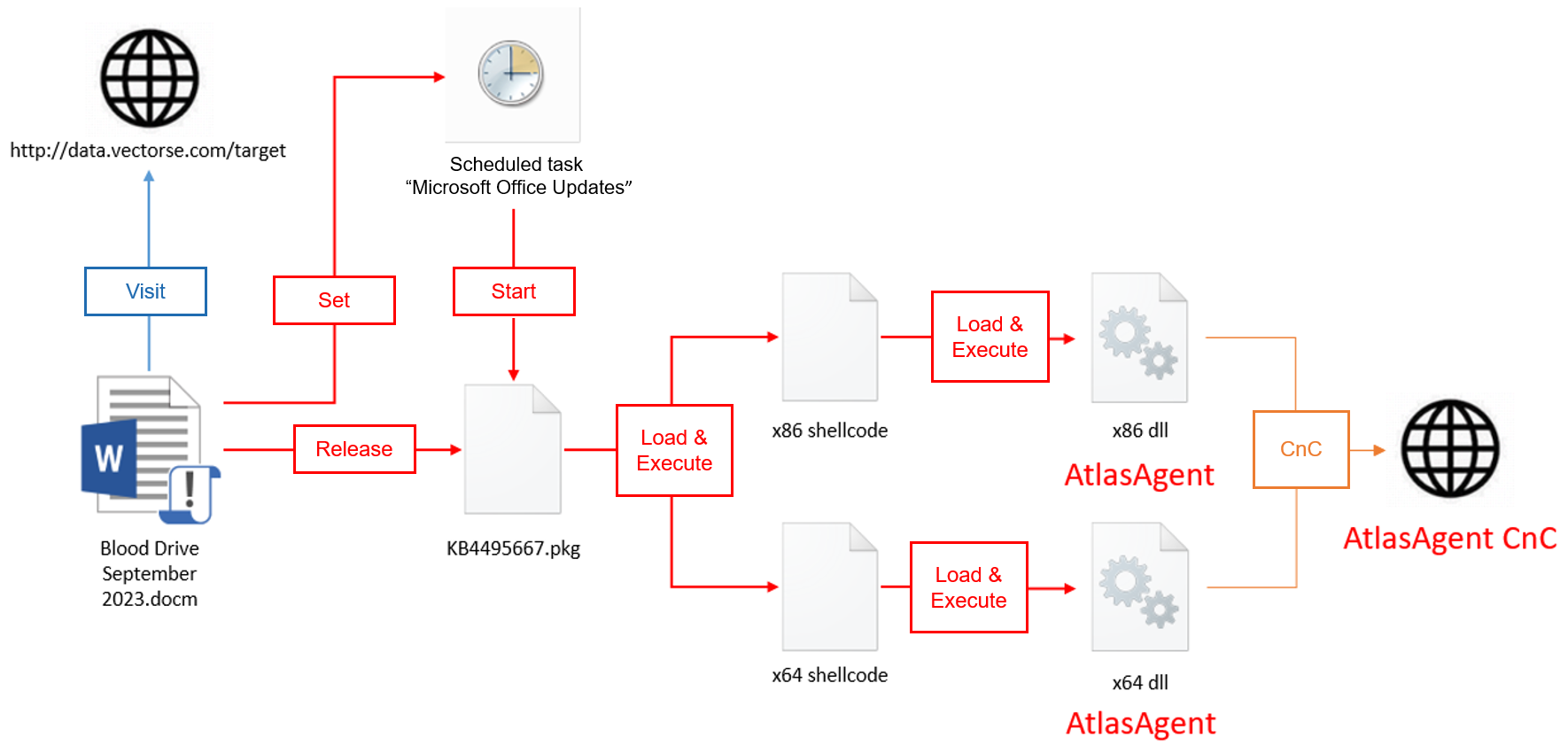
AtlasCross has left a trail of cyberattacks characterized by their use of cleverly designed phishing lures. One of their modus operandi involves crafting deceptive Microsoft documents, often masquerading as benign topics such as a blood donation drive organized by the American Red Cross. These documents are embedded with malicious macros that, when executed, set their malicious operations in motion.
Upon opening, victims are prompted to enable macro functionality, which initiates the execution of the attacker’s payload. This seemingly innocuous document becomes the entry point for AtlasCross to infiltrate and compromise targeted networks.
DangerAds and AtlasAgent: The Trojan Horse Duo
What sets AtlasCross apart from other threat actors is their innovative use of malware. Their arsenal includes two previously undocumented backdoors named DangerAds and AtlasAgent. These malicious programs work in tandem to achieve the attacker’s goals.
DangerAds serves as the initial loader, extracting and executing shellcode that ultimately leads to the deployment of AtlasAgent. This C++ malware is a versatile tool for AtlasCross, capable of gathering system information, executing shellcode, and running commands to obtain a reverse shell. Additionally, it can inject code into a thread within a specified process, allowing for covert operations.
Evasion Tactics
To avoid detection by security tools, both DangerAds and AtlasAgent incorporate evasion features. These tactics include:
Process Injection: AtlasAgent implements an injection method based on kernel-layer functions, bypassing user-layer API hooks and making it harder to detect.
Reflective Loading: Using open-source solutions like sRDI, AtlasCross loads DLL programs reflectively, reducing the likelihood of exposure caused by additional file and process operations.
API Confusion: AtlasAgent encrypts sensitive APIs using two encryption methods, increasing the difficulty of analysis and evading anti-virus and endpoint detection systems.
Anti-virtualization and Anti-sandbox: DangerAds is designed to run only when a specific username or local domain name is detected, effectively preventing execution in virtualized environments.
Resource Development and Persistence
AtlasCross employs a multi-pronged strategy, which includes resource development and persistence. The group takes control of public network hosts by exploiting vulnerabilities and transforming them into command-and-control (C2) servers. These compromised servers share commonalities, such as using specific software versions and configurations, making them valuable assets for the group.
The Enigmatic AtlasCross
One of the most intriguing aspects of AtlasCross is its enigmatic identity. Despite the extensive research conducted by cybersecurity experts, this threat group’s true origin and backers remain a mystery. They have managed to maintain a low profile while executing highly sophisticated attacks.
Conclusion
AtlasCross represents a new breed of APT groups, demonstrating a high level of technical prowess and a meticulous approach to cyberattacks. Their focus on targeted strikes within specific network domains, combined with their advanced attack techniques and evasion tactics, pose a significant challenge to cybersecurity professionals.