Researchers at Cisco Talos have uncovered a critical vulnerability in the Windows operating system that allows threat actors, primarily native Chinese speakers, to forge signatures on kernel-mode drivers. By exploiting this loophole, malicious actors can load unverified drivers with expired certificates, bypassing Windows’ driver signature enforcement. This article delves into the technical details of the loophole, the open-source tools employed for signature forging, the use of stolen and expired certificates, and the potential impact on Windows security.
Understanding the Windows Policy Loophole:
Windows divides its operating system into user mode and kernel mode, with kernel-mode drivers responsible for core system functionality. Microsoft introduced driver signature enforcement to maintain system integrity and security, requiring kernel-mode drivers to be digitally signed by trusted certificate authorities. However, an exception was made to maintain compatibility with older drivers, allowing newly compiled drivers signed with non-revoked certificates issued prior to or expired before July 29, 2015, as long as they chain to a supported cross-signed certificate authority.
Exploiting the Loophole with Open-Source Tools:
Threat actors leverage open-source tools such as HookSignTool and FuckCertVerifyTimeValidity to exploit the Windows policy loophole. HookSignTool, released in 2019, modifies the signing date of drivers during the signing process by hooking into the Windows API and manipulating the import table of legitimate code signing tools. FuckCertVerifyTimeValidity, introduced in 2018, bypasses time validity verification of certificates and allows custom dates to be specified.
Technical Details of HookSignTool:
HookSignTool employs Windows API hooking and import table alteration to manipulate the signing date of drivers. By attaching to the CertVerifyTimeValidity function, responsible for verifying certificate time validity, HookSignTool intercepts and changes the signing timestamp during execution. It also modifies the URL strings of timestamp authorities embedded within the legitimate signing tool to ensure the injection of a custom timestamp authority during the signing process.
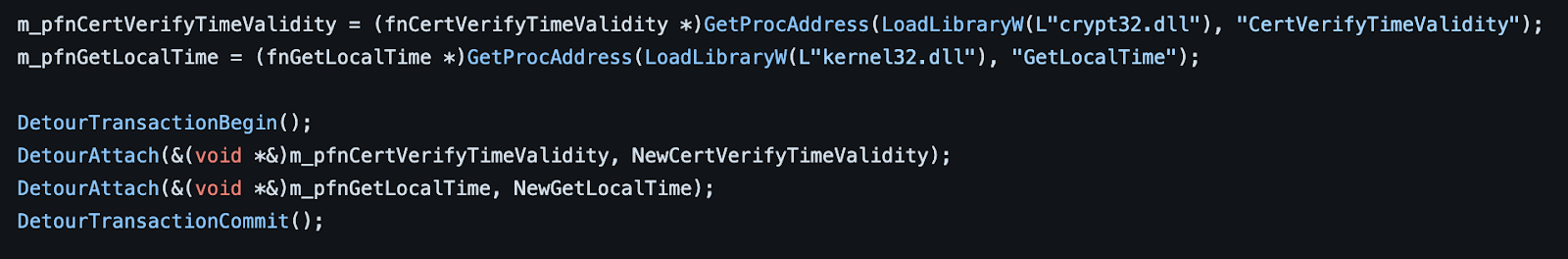
Technical Details of FuckCertVerifyTimeValidity:
FuckCertVerifyTimeValidity attaches to the CertVerifyTimeValidity API call using the Microsoft Detours package. It introduces a function into the import table of the legitimate signing tool, allowing it to modify the timestamp during execution. By making CertVerifyTimeValidity always return a valid result, FuckCertVerifyTimeValidity effectively bypasses the time validity check. It achieves this by installing a hook into CertVerifyTimeValidity and replacing it with a custom implementation.
Utilization of Stolen and Expired Certificates:
To successfully forge signatures, threat actors require non-revoked code signing certificates issued prior to or expired before July 29, 2015, along with their corresponding private keys and passwords. Cisco Talos discovered a PFX file on GitHub containing numerous expired code signing certificates frequently employed in signature forging. Some certificates were obtained from the 2015 Hacking Team leaks, while others originated from a leak on a Chinese software cracking forum.
Real-World Example: RedDriver:
RedDriver, a previously undocumented driver, utilizes HookSignTool for signature timestamp forging. This driver-based browser hijacker intercepts and redirects browser traffic to localhost. Its purpose remains uncertain, but it possesses the ability to manipulate browser traffic at the packet level.
Implications and Mitigation:
The exploitation of this Windows policy loophole highlights the importance of robust driver signature enforcement and continuous security updates. Microsoft has responded by blocking the certificates associated with this vulnerability and suspending developer program accounts involved. Organizations and users must remain vigilant, keeping their systems updated with the latest security patches to mitigate the risk of such malicious drivers.


