In cybersecurity, new threats emerge, and attackers constantly evolve their tactics. Recently, researchers unveiled a novel category of threats known as RAT-as-a-Ransomware. However, a recent discovery has shed light on another hybrid threat called Stealer-as-a-Ransomware. This article delves into the details of RedEnergy Stealer, a sophisticated malware that combines silent data theft with encryption, posing a significant risk to various industries.
Discovery of RedEnergy Stealer:
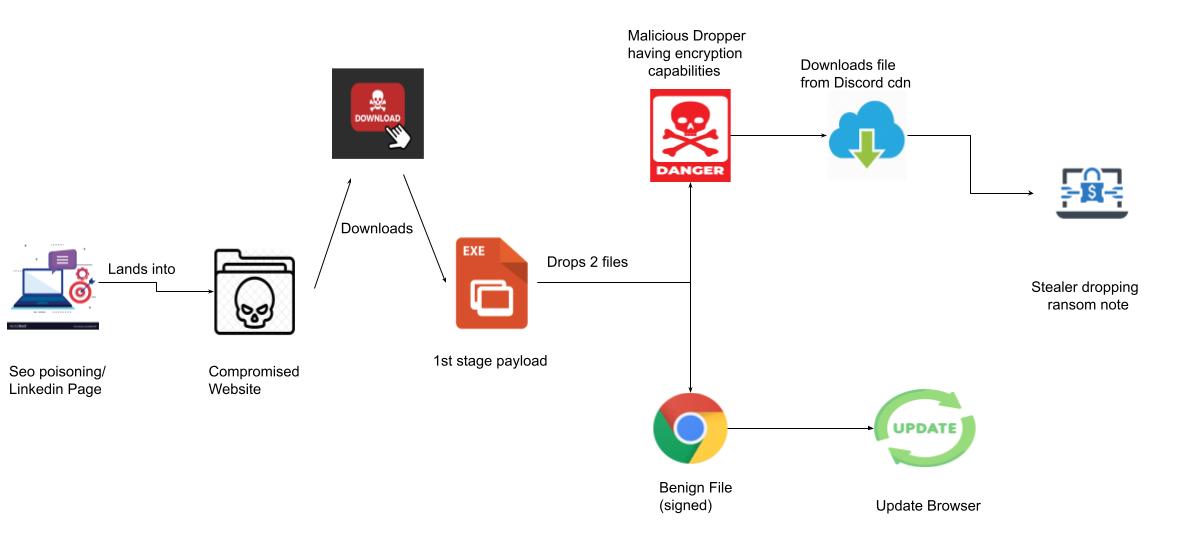
During the cybersecurity event Botconf 2023, ThreatLabz introduced the concept of RAT-as-a-Ransomware. Following a similar approach, a new category called Stealer-as-a-Ransomware was identified. RedEnergy Stealer, a prime example of this category, targets industries such as energy utilities, oil, gas, telecom, and machinery. It utilizes a deceptive FAKEUPDATES campaign to trick victims into updating their browsers, ultimately leading to data theft and file encryption.
Stealer-as-a-Ransomware: A Disturbing Evolution:
RedEnergy Stealer represents a notable evolution in ransomware attacks. It can act as a stealer and ransomware, employing obfuscation techniques and utilizing HTTPS for communication. These features make detection and analysis challenging for security professionals.
Multi-Stage Execution:
The malware operates through multiple stages, starting with disguised malicious executables. It establishes persistence, communicates with DNS servers, and downloads additional payloads from remote locations. Suspicious FTP interactions suggest potential data exfiltration and unauthorized file uploads.
Ransomware Functionality:
RedEnergy Stealer includes ransomware modules that encrypt user data, rendering it inaccessible until a ransom is paid. It employs tactics such as modifying the desktop.ini file to evade detection and modifying file system folder display settings.
Deletion of Shadow Drive Data:
The malware deletes shadow drive data and Windows backup plans in its final stage, reinforcing its ransomware characteristics. It drops a batch file and a ransom note, demanding payment in exchange for file decryption.
Campaigns Exploiting FAKEUPDATES:
Apart from the specific case involving the Philippines Industrial Machinery Manufacturing Company, other related campaigns exploiting the FAKEUPDATES tactic have been discovered. These campaigns impersonate reputable companies, such as a Brazilian telecom company and a Brazilian cosmetics company, to deceive users and distribute the same payload as RedEnergy Stealer.
Technical Analysis:
The RedEnergy malware possesses advanced capabilities to evade detection and hinder analysis. It utilizes HTTPS for command and control communication, adding an extra layer of encryption and obfuscation. The execution of the malware occurs in three stages: Initial Startup, Dropping Files, Persistence, Outgoing Requests, and Encrypted Files.
Conclusion:
RedEnergy Stealer and its hybrid nature present a significant threat to industries targeted by this malware. Organizations can enhance security measures and protect against similar malware campaigns by understanding their operational aspects and technical behavior. Vigilance in verifying browser updates, cautious web browsing, and prompt incident response are crucial in mitigating the risks associated with this ongoing threat.

