RomCom Cyber Attack Targets Ukraine Supporters During NATO Summit

The BlackBerry Threat Research and Intelligence team has uncovered a targeted cyber attack campaign involving the RomCom threat actor group. The attack aims to compromise individuals and organizations supporting Ukraine and is timed to coincide with the upcoming NATO Summit in Vilnius.
Attack Details:
The RomCom threat actor group has sent two malicious documents as lures, one targeting an organization supporting Ukraine abroad and the other focusing on guests attending the NATO Summit. These documents impersonate legitimate entities such as the Ukrainian World Congress and contain malicious content.

Infection Technique:
The initial infection vector is not yet identified, but the threat actors likely used spear-phishing techniques. Victims are directed to click on specially crafted replica websites that mimic legitimate organizations. The fake websites utilize typosquatting techniques, making them appear legitimate to unsuspecting users.
Exploitation and Payload:
Once the victim opens the malicious documents, an execution sequence is triggered involving the exploitation of a patched vulnerability known as Follina (CVE-2022-30190) in Microsoft’s Support Diagnostic Tool (MSDT). This vulnerability allows the threat actors to achieve remote code execution. The payload deployed is the RomCom Remote Access Trojan (RAT), an executable in C++. The RAT collects information about the compromised system and enables remote control by the threat actors.
Network Infrastructure and Attribution:
The RomCom threat actor group operates a command-and-control (C2) infrastructure that overlaps with previously known RomCom campaigns. The network infrastructure used in this attack shows similarities and connections to RomCom operations. The analysis concludes that the RomCom group or its members are likely behind this campaign.
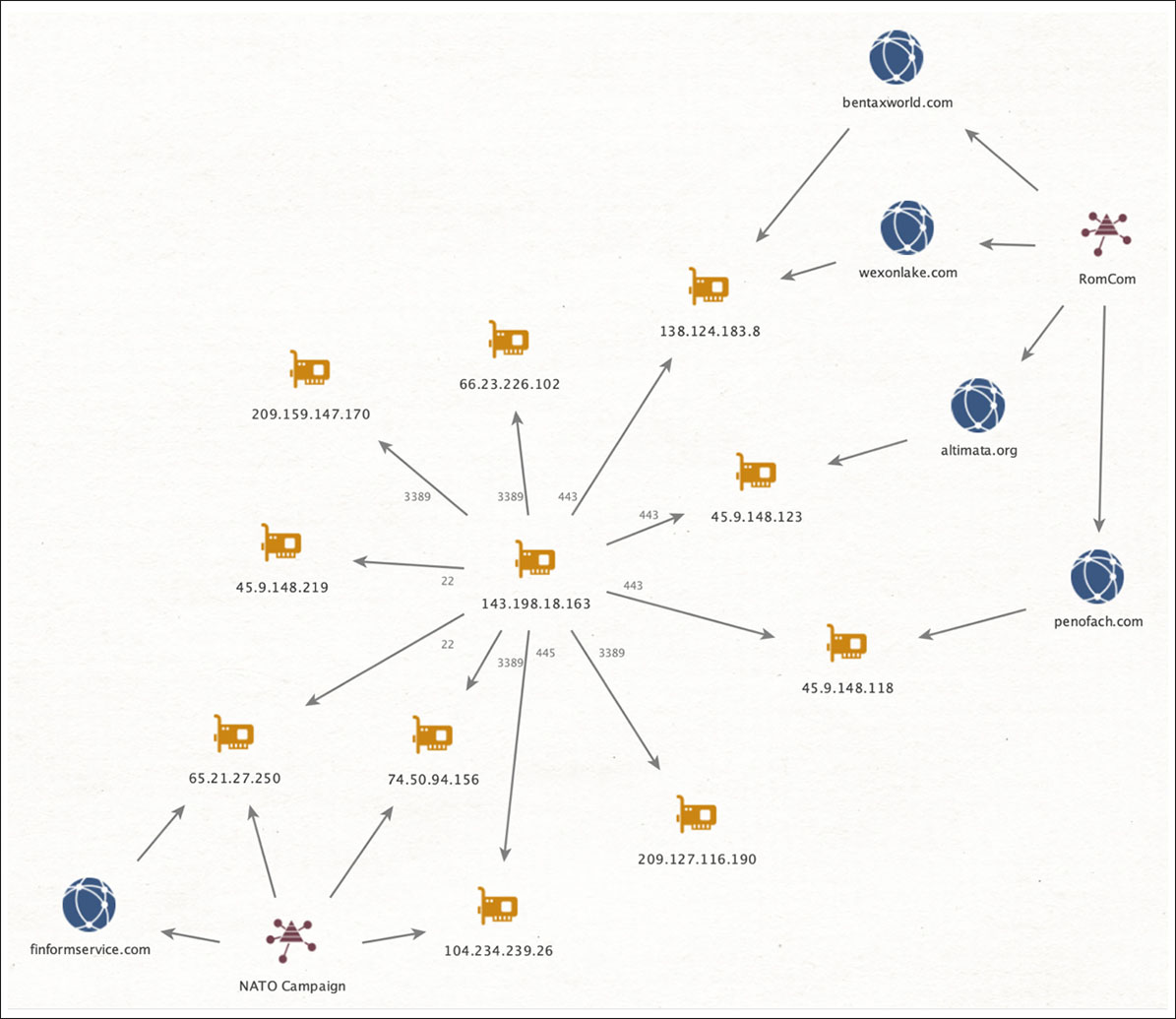
Targets and Motivation:
The main targets of this attack are representatives of Ukraine, foreign organizations supporting Ukraine, and individuals associated with Ukraine. The attack is motivated by the upcoming NATO Summit and the discussions around Ukraine’s potential membership in NATO.
Conclusion:
A cyber attack campaign orchestrated by the RomCom threat actor group targets Ukraine supporters and organizations involved with the upcoming NATO Summit. The attack utilizes spear-phishing techniques, exploits a patched vulnerability, and deploys the RomCom RAT as the payload. It is highly likely that the RomCom group or its members are responsible for this campaign. The nature of the attack highlights the geopolitical motivations behind the RomCom operations.
