Realst Malware: Targeting Apple macOS Systems and Stealing Cryptocurrency Wallets

The world of cyber threats constantly evolves, and Apple macOS users now face a new menace known as “Realst” malware. This sophisticated malware, written in the Rust programming language, targets both macOS and Windows systems with a specific focus on infecting macOS 14 Sonoma, the upcoming major release of the operating system. Disguised as fake blockchain games, Realst is adept at emptying crypto wallets and stealing stored passwords and browser data, posing a significant threat to cryptocurrency users. Realst was first discovered by security researcher iamdeadlyz.
The Modus Operandi of Realst Malware
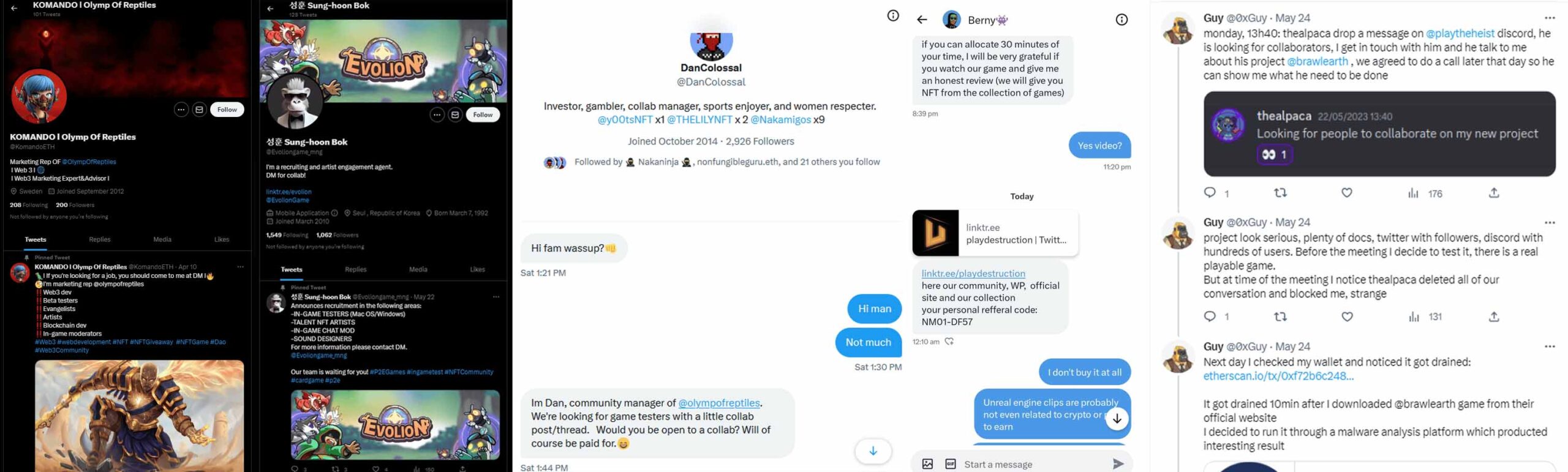
Realst Infostealer is distributed through deceptive websites advertising counterfeit blockchain games with alluring names such as Brawl Earth, WildWorld, Dawnland, and more. These malicious websites even come with associated Twitter and Discord accounts, creating an illusion of legitimacy for unsuspecting victims. The threat actors employ direct messages on social media to approach potential victims, enticing them to test the fake game as part of a paid collaboration. Upon execution, the malware springs into action, infiltrating the victim’s system and compromising their sensitive information.
Cross-Platform Capabilities and Variants
Though Realst is written in the Rust programming language, it predominantly targets macOS systems, with no significant presence on other platforms. The development team behind Realst possesses in-depth knowledge of the macOS environment, making it a tailored and potent threat. SentinelOne has identified 16 variants of Realst across 59 samples, revealing the threat actor’s commitment to targeting macOS users for data and cryptocurrency theft.
Realst’s Stealthy Approach
The malware employs several techniques to steal valuable data and evade detection:
Browser Data Harvesting: Realst targets popular web browsers like Brave, Google Chrome, Mozilla Firefox, Opera, and Vivaldi to gather sensitive information.
Exclusion of Apple Safari: Notably, Realst avoids targeting Apple Safari, leaving macOS users on this browser temporarily unscathed.
Password Spoofing: The malware attempts to extract user passwords through AppleScript spoofing and osascript.
Virtual Machine Detection: Realst incorporates rudimentary checks to ensure it does not run on virtual machines, increasing its chances of infecting real macOS systems.
Differentiating Realst from RedLine Stealer
Realst malware demonstrates that the threat actors possess a profound understanding of macOS, making it vastly different from RedLine Stealer, which targets Windows systems. Both malware families are part of a broader information-stealing campaign and share links to Pureland, a previous information stealer discovered in March. Realst’s rapid development and cross-platform capabilities highlight the significant efforts invested by the threat actors to target macOS users successfully.
Protecting Against Realst Malware
As Realst continues to threaten macOS users, taking proactive measures to safeguard personal information and cryptocurrency assets is crucial. Users are advised to be cautious when encountering blockchain games promoted through social media channels, especially those with “verified” Twitter accounts and Discord presence. Additionally, regularly updating operating systems, browsers, and security software can help mitigate the risk of falling victim to such malware. Implementing multi-factor authentication (MFA) and avoiding downloading files from untrusted sources are essential practices for bolstering cybersecurity.
Conclusion
The emergence of Realst malware has added a new layer of complexity to the cybersecurity landscape, with its ability to target Apple macOS systems and upcoming releases like Sonoma. Users must remain vigilant, exercise caution when encountering suspicious links or files, and stay up-to-date with the latest security measures. By being proactive in their approach to cybersecurity, macOS users can protect their cryptocurrency wallets, sensitive information, and financial assets from this formidable threat.