A new malware tool called EvilExtractor has emerged in the cybercrime world. Developed by Kodex as an “educational” tool, it was discovered by FortiGuard Labs being used as an info stealer. EvilExtractor targets Windows operating systems and extracts data and files from endpoint devices via an FTP service. It contains modules that allow it to steal data from compromised endpoints and upload it to the attacker’s FTP server. Its primary purpose is to steal browser data and information.
EvilExtractor was released in October 2022, and since then, the developer has been continually updating it to increase its stability and strengthen its module. FortiGuard Labs observed increased malicious activity in March 2023, indicating that cybercriminals are actively using it.
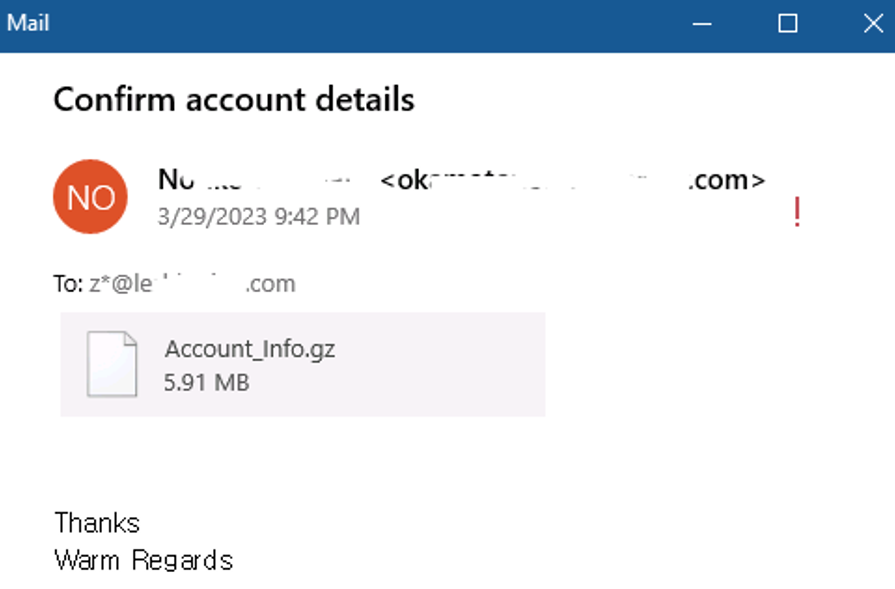
The initial attack method for delivering EvilExtractor is through a phishing email campaign. The email contains an attachment disguised as an account confirmation request and uses an Adobe PDF icon. The execution file is a Python program packaged by PyInstaller, with a “PYARMOR” string, an obfuscating tool for Python scripts. EvilExtractor contains a .NET loader that can extract it. This loader contains Base64-encoded data, which is a PowerShell script generated from the tool “PS2EXE-GUI,” used to convert PowerShell scripts to EXE Files.
EvilExtractor contains several modules: date time checking, anti-sandbox, anti-VM, anti-scanner, FTP server setting, steal data, upload stolen data, and clear log. The first check it performs is whether the system’s date is between 2022-11-09 and 2023-04-12. If not, it deletes the data in PSReadline and terminates. It then compares the product model to virtual environments such as VirtualBox, VMWare, Hyper-V, Parallels, Oracle VM VirtualBox, Citrix Hypervisor, QEMU, KVM, Proxmox VE, or Docker. It also checks the victim’s hostname against 187 names from VirusTotal machines or other scanner/virtual machines.
EvilExtractor downloads three components for stealing data. The first, KK2023.zip, is used for stealing browser data, including cookies, browser history, and passwords from Google Chrome, Microsoft Edge, Opera, and Firefox, and saving them in the folder “IMP_Data”. The second, Confirm.zip, is a keylogger that saves data in the “KeyLogs” folder. The last file, MnMs.zip, is a webcam extractor. EvilExtractor also collects system information by PowerShell script and downloads files with specific extensions from the Desktop and Download folders.
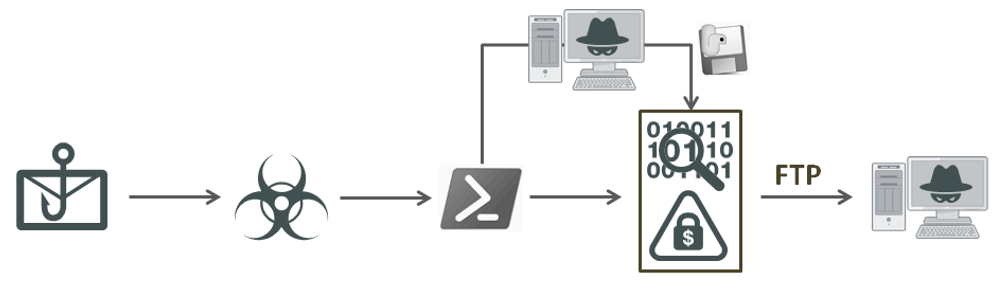
Most of EvilExtractor’s victims are located in Europe and America. Cybercriminals are using this tool to extract data and files from Windows operating systems via FTP service, and it poses a severe threat to individual users and organizations. The attack method used to deliver EvilExtractor is a phishing email campaign, indicating the importance of cybersecurity awareness and education.
In conclusion, EvilExtractor is a malicious attack tool that steals data and files from Windows operating systems. It contains several modules and can perform environment checks, steal browser data, and extract data from keyloggers and webcams. To protect against this tool, individuals and organizations should remain vigilant, practice safe browsing habits, and ensure their systems are up-to-date with the latest security patches.