Windows users face a new wave of cyber threats as sophisticated malware named LokiBot spreads through malicious Microsoft Office documents. A recent investigation by FortiGuard Labs has uncovered that attackers are exploiting well-known vulnerabilities such as CVE-2021-40444 and CVE-2022-30190 to deliver the LokiBot malware. LokiBot, a notorious information-stealing Trojan active since 2015, specializes in extracting sensitive information from compromised Windows systems.
Exploiting Microsoft Office Vulnerabilities:
The malicious Office documents identified in the investigation utilize two specific vulnerabilities: CVE-2021-40444 and CVE-2022-30190. These vulnerabilities, known as remote code execution flaws, allow the attackers to embed malicious macros within the documents, leading to the deployment of LokiBot on victims’ systems. CVE-2021-40444 involves an external link embedded within an XML file, while CVE-2022-30190 exploits a VBA script executed through a macro.
Attack Chain Analysis:
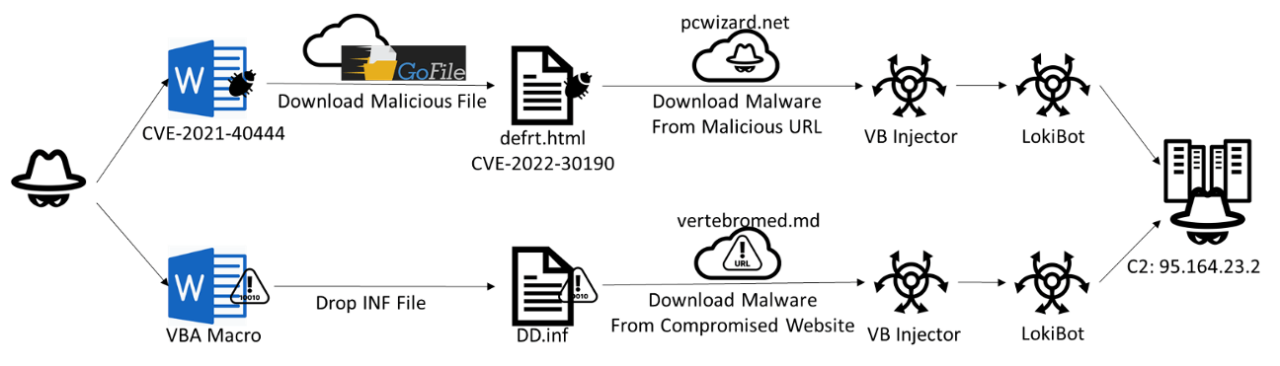
The investigation revealed two distinct attack chains employed by the malicious documents. The first chain utilizes an external link within the XML file, redirecting users to a cloud file-sharing website called “GoFile.” From there, a file named “defrt.html” is downloaded, exploiting CVE-2022-30190. This file triggers the download of an injector file, “oehrjd.exe,” from a specific URL.
The second attack chain involves a Word document with an embedded VBA script that executes a macro upon opening. This script decodes various arrays and saves them to a temporary folder, eventually leading to the download and execution of LokiBot.
Evasion Techniques and Command-and-Control Infrastructure:
To evade detection and analysis, LokiBot employs various evasion techniques. These techniques include checking for the presence of debuggers, verifying virtual machine paths, and using sleep functions to determine if time acceleration has occurred. LokiBot’s command-and-control (C2) infrastructure plays a crucial role in its operations, with connections made to specific IP addresses for communication and data exfiltration.
LokiBot’s Capabilities and Implications:
LokiBot is a powerful malware that targets sensitive information across various sources, including web browsers, FTP, email, and software tools. It can log keystrokes, capture screenshots, gather login credentials, and extract data from cryptocurrency wallets. The malware’s continuous evolution and the cybercriminals’ adaptability make it a significant threat to users and organizations.
Protective Measures and Best Practices:
To protect against LokiBot and similar threats, users should exercise caution when handling Office documents or unknown files, particularly those containing external links. Avoid clicking on suspicious links or opening attachments from untrusted sources. Additionally, keeping the software and operating systems up to date with the latest security patches is crucial to mitigating the risk of exploitation by malware.
Conclusion:
The discovery of LokiBot malware exploiting Microsoft Office vulnerabilities emphasizes the importance of maintaining robust cybersecurity practices. By understanding the attack chain and the behaviors exhibited by LokiBot, users, and organizations can enhance their defenses and protect against this persistent threat. Vigilance, cautiousness, and regular updates are essential to safeguarding sensitive data and preventing potential compromises.