Cyber threats have recently been evolving rapidly, with threat actors continuously adapting their tactics to exploit vulnerabilities. One such threat group that has caught the attention of cybersecurity experts is Storm-0324, also known as TA543 and Sagrid. Microsoft’s Threat Intelligence team has been closely monitoring Storm-0324, which has been actively involved in phishing campaigns and distributing malware payloads. This article will shed light on the tactics and evolution of Storm-0324, emphasizing its recent shift towards using Microsoft Teams as a platform for phishing attacks and the potential implications for organizations.
The Rise of Storm-0324
Storm-0324 is a financially motivated threat group that has gained notoriety for its involvement in cybercriminal activities. One of its primary tactics is gaining initial access through email-based phishing lures. Once inside a compromised network, Storm-0324 often hands off access to other threat actors, a move that frequently results in ransomware attacks. This escalation of attacks underscores the critical importance of identifying and mitigating Storm-0324’s activities early to prevent more destructive follow-on attacks.
Historical Malware Distribution
Storm-0324 has a history of employing a variety of malware strains and email-based phishing lures. Some of the malware used include Nymaim, Gozi, Trickbot, IcedID, Gootkit, Dridex, Sage ransomware, GandCrab ransomware, and JSSLoader. JSSLoader, in particular, has been a key component of its campaigns since 2019. This malware serves as an entry point for ransomware-as-a-service (RaaS) actor Sangria Tempest.
Phishing Lures and Infection Chains
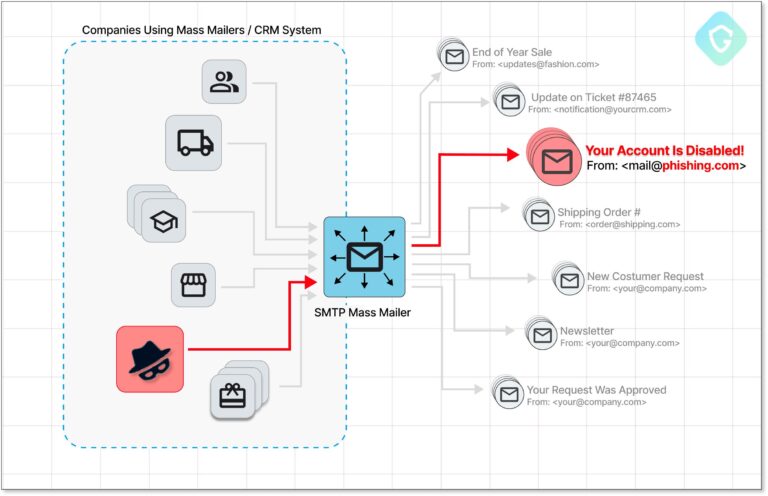
Storm-0324’s phishing lures are highly evasive and often impersonate legitimate services such as DocuSign and Quickbooks. These lures lead users to a SharePoint-hosted compressed file containing JavaScript, which downloads malicious DLL payloads. The group uses various file formats, including Microsoft Office documents, Windows Script Files (WSF), and VBScript, to execute the malicious code.
New Teams-Based Phishing Activity
In July 2023, Storm-0324 adopted a novel approach using Microsoft Teams as a vector for phishing attacks. Instead of relying solely on email-based tactics, the group leveraged an open-source tool called TeamsPhisher. This tool allows attackers to send malicious links through Microsoft Teams messages, directing victims to malicious SharePoint-hosted files.
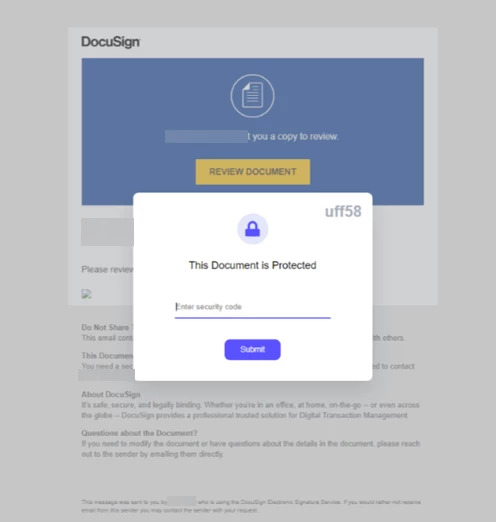
The use of TeamsPhisher marked a significant shift in Storm-0324’s tactics, as they now exploit the trust associated with communication platforms like Microsoft Teams. These phishing lures are identified by Teams as “EXTERNAL” users if external access is enabled in the organization, making it crucial for organizations to be vigilant.
Mitigating the Threat
To defend against the evolving threat posed by Storm-0324 and similar actors, Microsoft recommends several measures:
- Use Microsoft 365 Defender: Microsoft 365 Defender can help detect and limit the impact of Storm-0324’s activities on networks.
- Implement Least Privilege: Adhering to the principle of least privilege helps restrict attackers’ access, limiting their destructive capabilities even if they gain initial access.
- Enhance Credential Hygiene: Maintaining good credential hygiene can help prevent unauthorized access to sensitive systems.
- Phishing-Resistant MFA Methods: Organizations using Microsoft Teams should consider deploying phishing-resistant multi-factor authentication (MFA) methods, such as hardware security keys.
Conclusion
Storm-0324 represents a growing threat in the cybersecurity landscape. Its ability to adapt and evolve its tactics, including the use of Microsoft Teams for phishing campaigns, underscores the need for organizations to remain vigilant and proactive in their cybersecurity efforts. By staying informed about emerging threats and implementing robust security measures, organizations can better defend against the ever-changing tactics of threat actors like Storm-0324.