Chinese cyber espionage activities have evolved significantly in recent years, with threat actors employing advanced techniques to avoid detection and complicate attribution. Mandiant has recently disclosed these evolving tactics, focusing on exploiting zero-day vulnerabilities in security, networking, and virtualization software. Additionally, Chinese threat actors have increasingly targeted routers and utilized botnets to relay and disguise attacker traffic within victim networks.
Chinese Cyber Espionage and Zero-Day Exploitation:
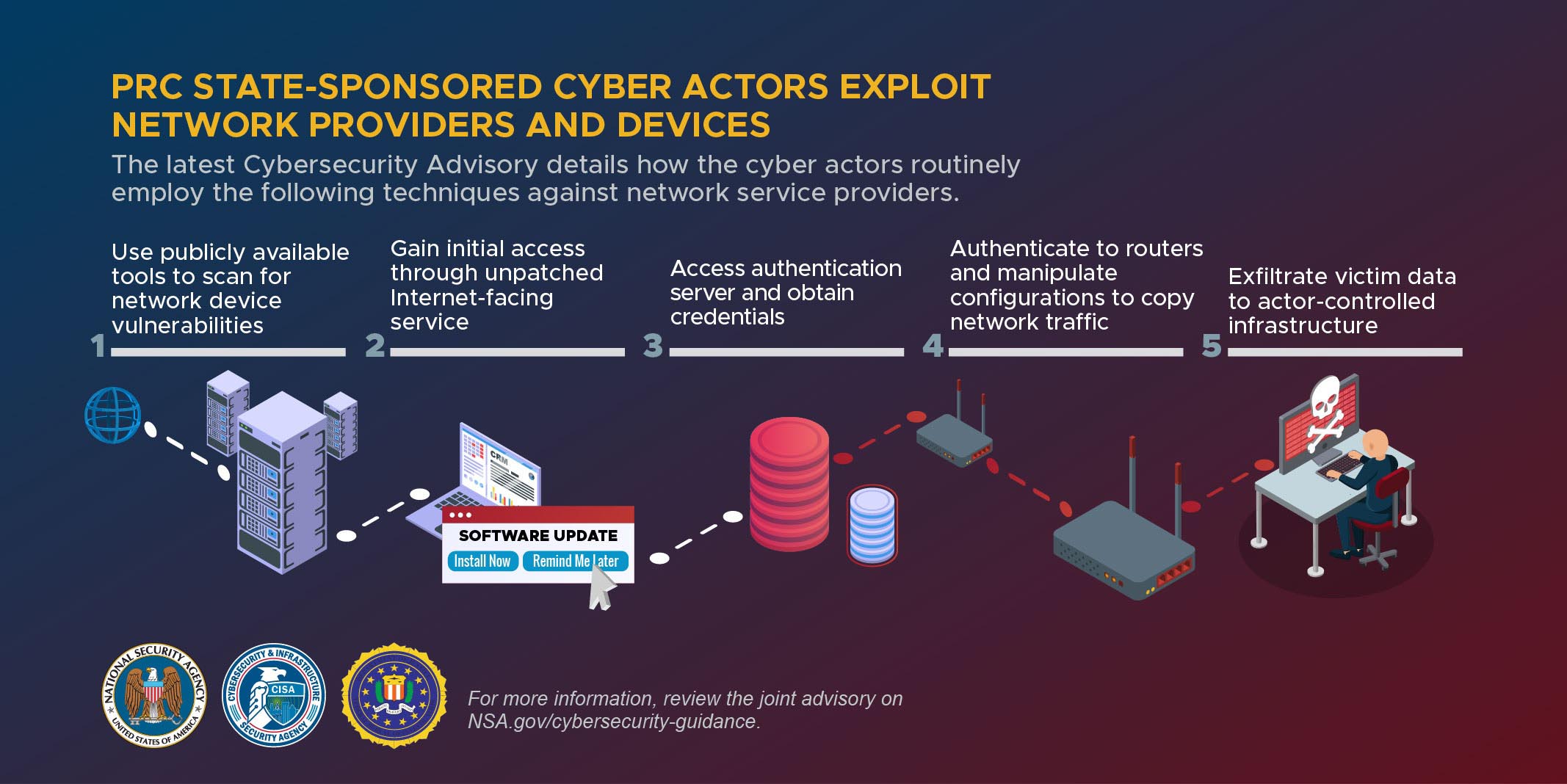
Chinese cyber espionage groups have increasingly leveraged zero-day vulnerabilities in security, networking, and virtualization technologies to gain and retain access to victim networks. These devices, such as security appliances and virtualization platforms, offer tactical advantages due to their accessibility and limited monitoring capabilities.
In a recent investigation, Mandiant uncovered the activities of UNC3886, a suspected Chinese cyber espionage actor. UNC3886 employed multiple attack paths and two zero-day vulnerabilities to establish persistence in targeted organizations and gain access to virtualized environments. The group focused on Fortinet security devices and VMware virtualization technologies to remain undetected, which traditionally lack endpoint detection and response (EDR) solutions. UNC3886 utilized custom malware and exploits that circumvented logs and security controls, including the use of non-traditional protocols that evade default logging and security restrictions. The threat actor also cleared and modified logs and disabled file system verification to avoid detection.
Another notable campaign involved UNC4841, which exploited a zero-day vulnerability in Barracuda Email Security Gateway (ESG) appliances. UNC4841 targeted public and private organizations globally, specifically interested in political and strategically important information. The threat actor employed various tactics to disguise its activity, including specially crafted email attachments and custom malware with naming conventions consistent with legitimate ESG files. UNC4841 also used legitimate self-signed SSL certificates and stolen certificates from victim environments to masquerade command and control traffic.
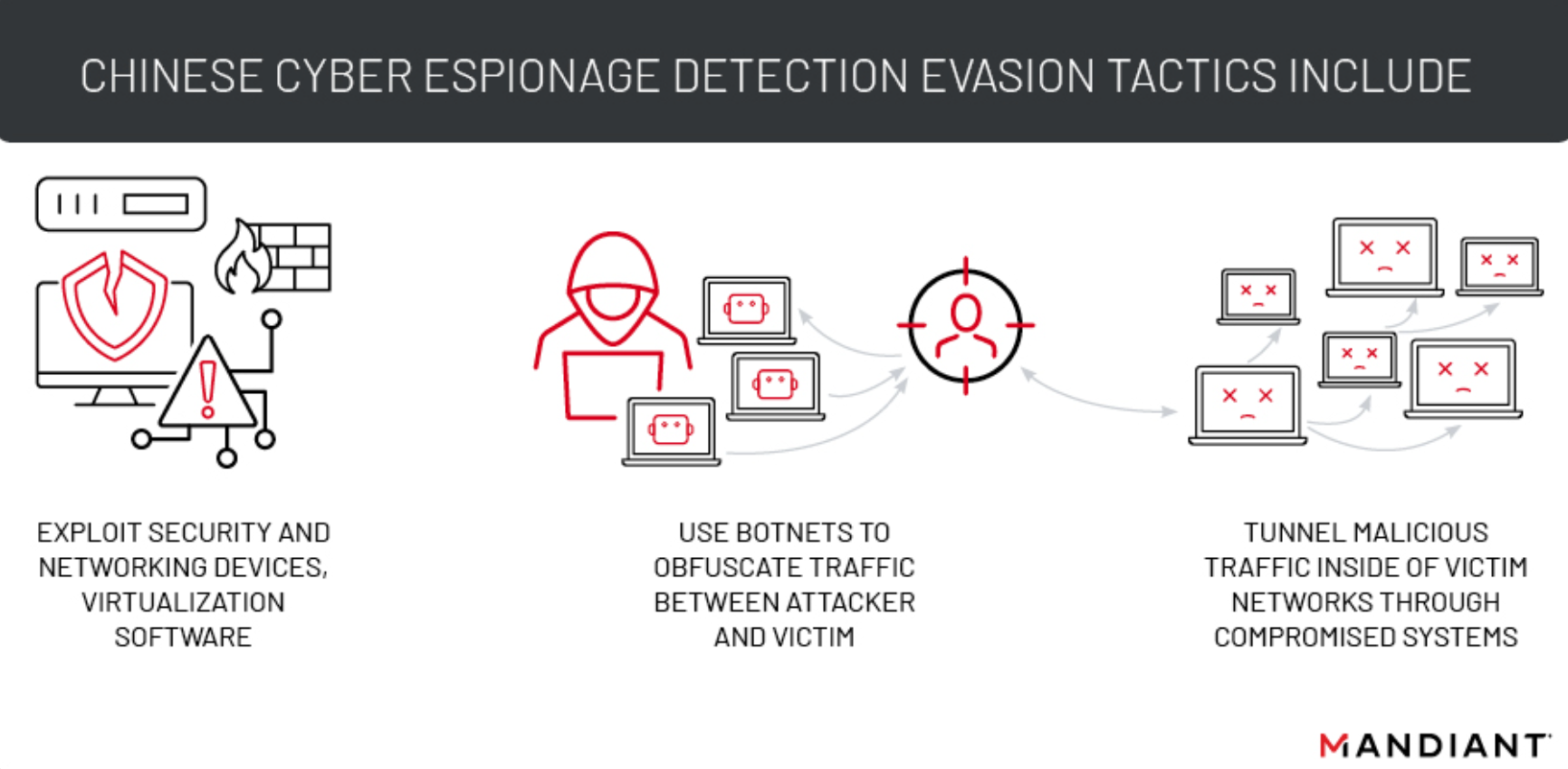
Use of Botnets and Traffic Disguise:
Chinese cyber espionage groups increasingly rely on compromised IoT devices, smart devices, and routers to create botnets that obfuscate external traffic between command and control (C2) infrastructure and victim networks. This tactic aims to evade detection and complicate attribution.
Mandiant identified several examples of Chinese threat actors employing botnets for traffic obfuscation. APT41, APT31, APT15, TEMP.Hex and Volt Typhoon are among the groups observed using botnets in their operations. For instance, Volt Typhoon, a state-sponsored Chinese hacker group, targeted critical infrastructure organizations in the United States, leveraging a botnet of compromised SOHO devices to route network traffic.
Implications and Conclusion:
Adopting advanced evasion techniques and zero-day exploitation by Chinese cyber espionage groups underscores their commitment to achieving higher success rates in gaining and maintaining access to valuable networks. The evolution of tactics, coupled with the country’s military and intelligence restructuring, shared development infrastructure, and legal and institutional structures, points to long-term investments in equipping Chinese cyber operators with sophisticated tools and exploits.
Understanding these evolving tactics is crucial for organizations to enhance their cybersecurity defenses and prioritize countermeasures. By staying informed about emerging trends and remaining vigilant, organizations can better protect themselves against Chinese cyber espionage activities and mitigate potential risks to their critical infrastructure.